Google software-defined networking fabric includes a next-generation firewall called Google Cloud Firewall that is completely distributed, stateful, and enforced for each workload. You can offer powerful network threat prevention at cloud scale with Cloud Firewall’s operational simplicity.
Google are happy to inform that the Cloud Firewall’s fully qualified domain name (FQDN) capability is now generally available. Customers may normally access FQDN as part of the Cloud Firewall Standard tier, which also offers geolocation filtering and interaction with Google Cloud Threat Intelligence. Additionally, Google added additional IP reputation lists to our support for Google Cloud Threat Intelligence and made IPV6 and GKE node pool support for IAM-governed tags available in Public Preview.
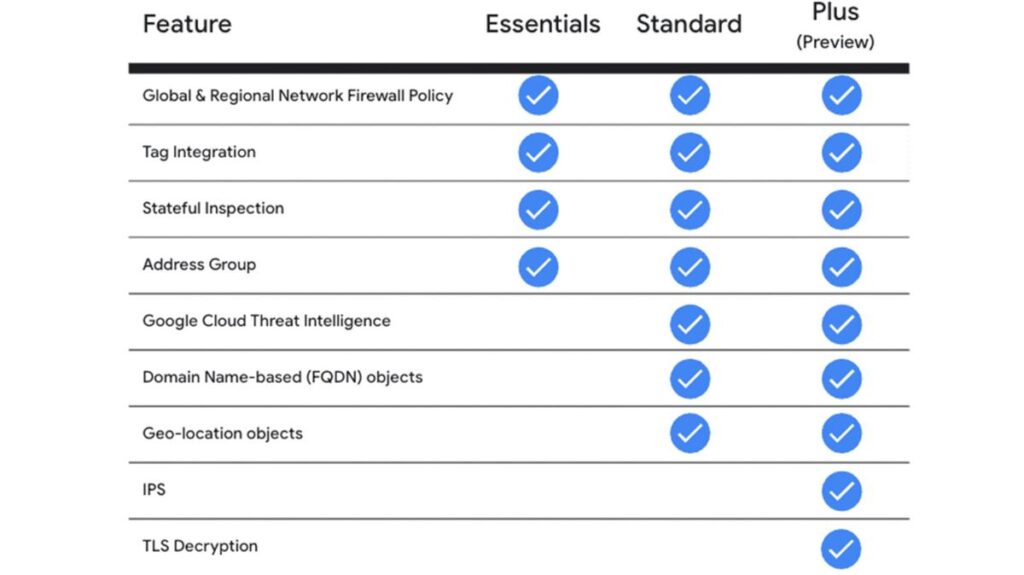
The following image illustrates the three levels of Cloud Firewall functionality that are available: The three sets of capabilities are Essentials the basic set Standard which broadens rule capabilities and Plus which adds sophisticated threat prevention capabilities. To find out more about the features in Plus tier, visit our Cloud Firewall Plus blog.
FQDN-based objects to facilitate domain name-based traffic filtering
When creating firewall rules for fully qualified domain name (FQDN)-based objects, Google Cloud takes care of identifying the precise IP addresses for the FQDN. The following advantages may result from using these objects in rules that allow or deny traffic based on FQDNs rather than IP addresses:
- Improved reliability: An increase in dependability since FQDNs remain constant while underlying IP addresses change. By doing so, you may be able to decrease downtime and increase access dependability to your cloud workloads.
- Easier to use: FQDNs are simpler to utilize since they are easier to memorize and more understandable by humans than IP addresses. By having your firewall rules self-documenting, you may improve their readability and make them simpler to audit and manage.
- Enhanced security: By making DNS spoofing attacks more difficult, Cloud Firewall works with Cloud DNS for FQDN name resolution to assist increase the security of your applications.
For Cloud Firewall, expanded threat intelligence listings
To assist you block known dangerous traffic and enable known benign traffic, Threat Intelligence for Cloud Firewall uses a mix of Google, third-party, and open source data to deliver curated IP reputation lists. Google Cloud Threat Intelligence researchers regularly update and maintain these lists.
With the following additional IP lists for Cloud Firewall, Google are extending their coverage of Threat Intelligence for Cloud Firewall, which is a component of the Cloud Firewall Standard tier. This will help you strengthen your security posture and assist prevent harmful traffic.
- iplist-vpn-providers: Matches IP addresses associated with VPN service providers with a bad reputation.
- iplist-anon-proxies: Matches IP addresses that are associated with open anonymous proxies using iplist-anon-proxies.
- iplist-crypto-miners: Ip addresses associated with cryptocurrency mining websites are matched by the iplist-crypto-miners tool.
- iplist-public-clouds-google-services: Matches IP addresses that are associated with Google services.
Improved tag support in firewall policies
Also available in public preview are support for IPv6 and node pools for IAM-governed tags on Google Kubernetes Engine (GKE). The Cloud Firewall Essentials grade offers tag support.
Prior until this, tags were only compatible with IPv4-based rules. You may now use tags as source and destination filters for IPv6-based rules since IPv6 now supports tags.
You may selectively apply Cloud Firewall network firewall rules in GKE clusters and node pools to assist manage traffic flow between your VM instances and GKE clusters and node pools thanks to GKE node pool support for resource management tags. By allowing micro-segmentation all the way down to the GKE node pool level, this improves your security posture.
Take action now
Stateful, scalable, cloud-first firewall solution with top-notch security features is called Cloud Firewall. The most recent Cloud Firewall Standard improvements, which are now GA-ready, provide you more features to streamline firewall operations and safeguard your cloud workloads.
Check out the most recent video or the manual to learn more about Cloud Firewall before turning it on in your cloud environment to protect your Internet traffic.


[…] firewall. With its high port density and tuned for maximum flexibility and scalability, the new Firewall 4200 Series can expand massively. It can also cluster up to 16 firewall devices together to function […]
[…] application firewall. Enterprise: APIs are protected against injection attacks, XSS, and CSRF by WAFs. WAF may analyze […]
[…] resource files from IaC execution and import them to firewall systems to automate […]