What is DNSSEC?
A feature of the Domain Name System (DNS) that verifies answers to domain name lookups is called Domain Name System Security Extensions (DNSSEC). Although it keeps attackers from tampering with or contaminating DNS query responses, it does not offer privacy protections for those lookups.
Not really. DNSSEC uses a different method than encryption public key cryptography to defend networks from man-in-the-middle attacks. Put differently, Domain Name System Security Extensions offers an authentication method but not a confidentiality method.
DNSSEC: Internet Foundation Protection
Domain Name System (DNS) converts human-readable domain names into machine-readable IP addresses for online security in the digital age. Security issues make traditional DNS vulnerable to manipulation and attacks. DNSSEC safeguards DNS data.
Major Advantages of DNSSEC:
DNSSEC uses public-key cryptography and digital signatures to verify DNS responses. This means a domain name’s IP address is authentic and hasn’t been changed from the authorized source.
Data Integrity: Phishing attempts and malicious website redirects can result from DNS data manipulation. DNSSEC prevents hackers from altering vital DNS records by cryptographically verifying them.
Middleman (MitM) Attack Prevention: DNSSEC guarantees authenticity and data integrity, reducing the risk of MitM attacks, in which attackers intercept and alter DNS responses to trick users.
Domain Name System Security Extensions protects DNS lookups from malicious and tampering, giving users and organizations confidence to use online services.
Is DNSSEC important?
Public/Private Key Pairs: Public keys are published in the DNS by domain owners, while private keys are kept confidential.
Digital Signatures: By digitally signing DNS records with the private key, a “fingerprint” that confirms their legitimacy is created.
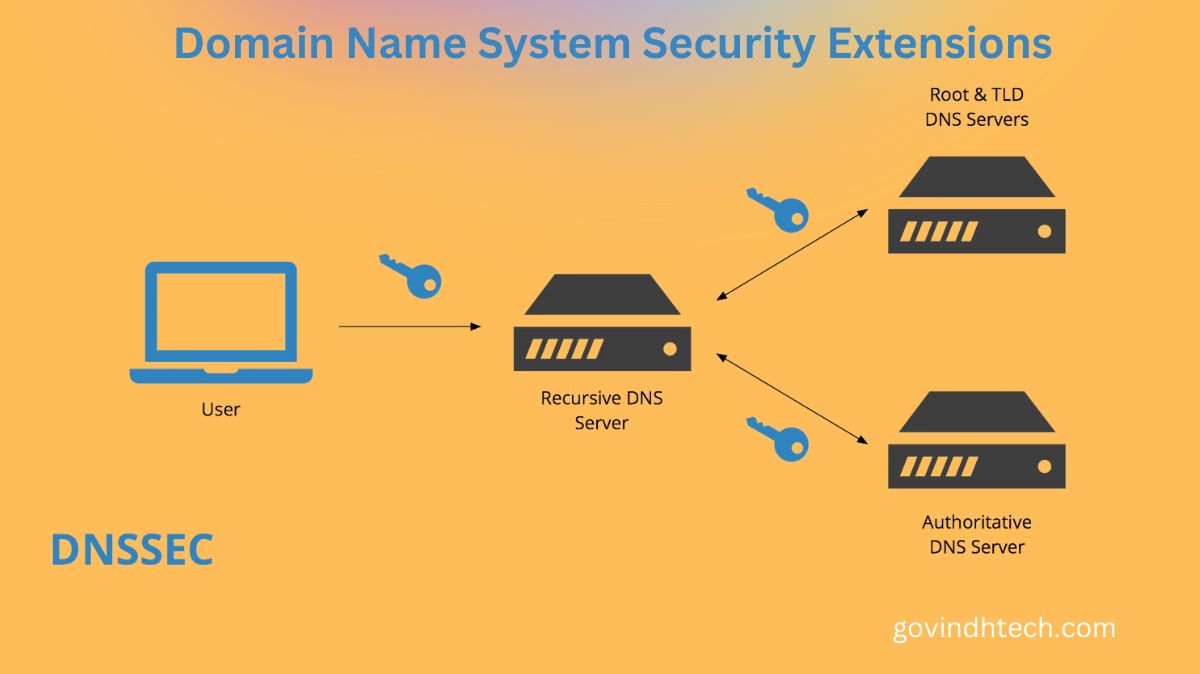
Signature Validation: To make sure received DNS records haven’t been tampered with, resolvers the programs that convert domain names into IP addresses verify the signatures using the public key that has been released.
Chain of Trust: Signatures are verified through a chain of trust that originates from the root of trust that is present at the top of the DNS hierarchy.
How to implement DNSSEC
Adoption: DNSSEC is being implemented more often, despite not being widely used. It is supported by a large number of prominent domain registries and registrars, and it is frequently free for organizations to enable.
Benefits Exceed Difficulties: Although DNSSEC setup and configuration may call for some technical know-how, the advantages greatly exceed the drawbacks. Organizations that are concerned about security ought to give it serious consideration for their domains.
What distinguishes public key cryptography from encryption?
DNS queries are digitally “signed,” or authenticated, using public key cryptography by DNSSEC. The receiving device can compare the data it receives with the original data sent by the authoritative server when DNSSEC is enabled on a zone record. A digital signature that authenticates data using public keys makes this possible.
The data in DNSSEC is not encrypted; instead, the authentication keys are secured through cryptography. Traffic protected by Domain Name System Security Extensions can still be intercepted and read. The receiving server will be able to detect that something is wrong if the data is altered somewhere along the data pathway and sent on to its destination because the public keys will not match.
On the other hand, encryption encrypts the data by using cryptography. By altering what an attacker would see if they were to intercept a query somewhere along the data pathway, encryption ensures confidentiality. Until the attacker uses an encryption key to decipher the signal, it renders the data unintelligible. Data is shielded from manipulation by encryption because the key isn’t disclosed to the public.
What is DNSSEC in cybersecurity?
Among the Internet’s more traditional protocols is DNS. The Internet was much smaller when it was first developed, and almost everyone there was acquainted. Data Security was not given much thought.
DNS was used so extensively by then that any major alteration would have brought down the entire system, even before the issue of Internet security arose. Instead of attempting to create a completely encrypted protocol to take the place of DNS, an authentication mechanism was added to the pre-existing system.
DNSSEC was vulnerable. By enabling the authentication of queries and data, it improved protocol security. However, it did so without altering the underlying architecture, allowing the Internet to expand further without requiring any new engineering. Domain Name System Security Extensions deployment was left optional so that organizations could make the switch whenever they felt ready.
If DNSSEC isn’t encrypted, why use it?
One major reason to use DNSSEC is to prevent DNS cache poisoning, also called DNS spoofing. A DNS spoofing attack involves replacing a legitimate DNS query response with an unauthenticated one. After that, the response becomes stuck in the cache, returning the incorrect response and sending users to malicious websites until the “time to live” runs out.
By authenticating DNS responses and guaranteeing that only accurate responses are returned, DNSSEC defends against these types of attacks. DNS spoofing attacks cannot be prevented by encryption, but it may safeguard the underlying data in a DNS connection.
Is DNSSEC still used if it isn’t encrypted?
Sadly, DNSSEC is only used to validate about 20% of Internet traffic. Even though it’s a big improvement over a few years ago, that amount is still far below what it ought to be. That substantial gap can be attributed to a combination of informational gaps, laziness, and usability issues.
By offering a straightforward deployment procedure, NS1 encourages all of its clients to implement DNSSEC. Through IBM’s Dedicated DNS offering- NS1 even offers Domain Name System Security Extensionsas a backup provider or redundant DNS option, in contrast to other providers.
Gazing Forward
Security continues to be the primary concern as the internet develops. One of the most important steps toward a more secure DNS ecosystem is Domain Name System Security Extensions. It encourages trust and confidence in online interactions by defending against critical vulnerabilities, protecting users and organizations from malicious activities.