Missed the Ignite breakout session on “Azure confidential computing and Intel: Technology for the AI era”? No problem. Intel will cover the announcement of new Confidential VM instances on Azure powered by Intel Trust Domain Extensions (Intel TDX) and other Confidential Computing announcements from Microsoft and Intel. This on-demand video features Intel’s VP and GM of Security and Systems Architecture, Anil Rao, and Microsoft’s Azure confidential computing Head of Product, Vikas Bhatia.
Data potential has arrived
For many applications, public cloud resources are cheaper and endlessly scalable than on-prem infrastructure. Multiple parties sharing data for analysis and solution development is an intriguing innovation field. As AI advanced, enormous amounts of data were needed to create new models, analysis, and solutions.
However, data is typically private or sensitive and regulated, making it difficult to maximize its value. New data protection solutions have addressed privacy, security, and compliance concerns, but there was always a gap. Before today, storage and disk encryption protected data at rest, and network encryption protected data in transit. When data is in use in the processor and memory, those methods fail. Off-storage and off-network vulnerability exists.
Data in use can be valuable to sophisticated hackers, nation-state actors, and hostile insiders. A service innovation may add value and convenience for users, but activating the data beyond a locked-down storehouse is often too risky, resulting in data silos and unrealized potential.
Azure confidential computing fills this gap in data protection, protecting data through the end.
Confidential computing?
Computing confidentiality serves three fundamental purposes.
1. Isolation:
A silicon-based Trusted Execution Environment (TEE) is used in confidential computing. Only software within the TEE’s trust boundary can decrypt sensitive data there. This technologically isolates protected content from software and admins outside the trust boundary. It’s even separated from the cloud provider’s management stack, hypervisor, and infrastructure admins.
2. Encryption/Control
Confidential Computing restricts data access to authorized users. Thus, data outside the TEE is encrypted and only approved software or parties can view it within. Your data cannot be accessed in plaintext by the cloud provider, other tenants, or users.
3. Verification:
Can you verify your TEE’s authenticity and functionality? Cryptographic verification of the TEE’s authenticity, policy updates, and, depending on the technology, software compliance are all part of confidential computing technology. This is called “Attestation.”
Intel SGX and TDX: TEE foundations
Intel has the largest secret computing portfolio to address modern enterprises’ various needs for TEEs. With hardware-based memory encryption Intel Software Guard Extensions (Intel SGX), Intel pioneered Confidential Computing for the data center by isolating application code and data in memory.
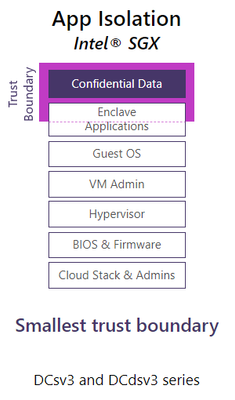
But Intel SGX was just the start. Microsoft Azure now offers Intel Trust Domain Extensions (TDX), VM isolation technology launched in 2023 by Intel.
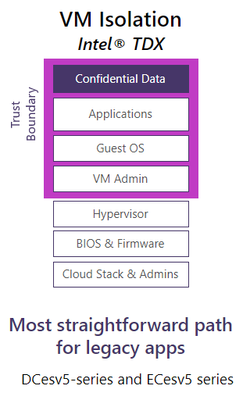
Intel’s unrivaled ecosystem, solution provider enabling, “security first” development methods, and best-in-class lifecycle security support support these products and services. Intel protects consumers long after they buy an Intel-based platform. Let’s discuss Intel Trust Authority’s additional protection.
Assurance from Intel Trust Authority
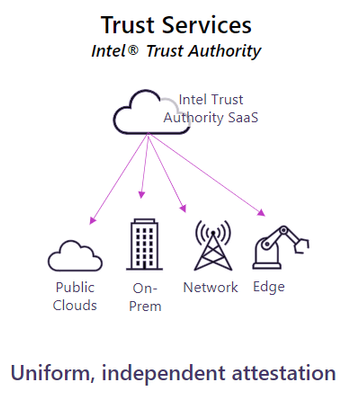
Attestation ensures that the cloud instance where you’re deploying sensitive data is what you anticipate. Intel Trust Authority delivers independent SaaS attestation services for public or private cloud, on-prem, and edge. It provides cryptographic proof of a secret computing environment independent of the cloud provider that any stakeholder can request at any time and confirms that:
- The TEE uses a genuine, security-enabled Intel CPU.
- The processor’s microcode patch is updated by policy.
- The TEE launched with authorized firmware.
- TEE software matches developer manifest and customer policy.
Intel Trust Authority verifies your security hardware.
Deeper Intel TDX confidence
Ephemeral VMs and OS disk integrity, Intel TDX secret VM security features in preview, can be used even if you missed the Ignite talk.
Ephemeral VMs add security when a confidential VM is stopped and revived. Cloud virtual machine (CVM) images could keep configurations, data, and secrets from the previous boot, exposing potentially confidential information. Intel TDX has an ephemeral virtual trusted platform module (vTPM) that does not store secrets like keys or configurations.
The OS disk integrity tool is an Azure CLI plugin that prepares, measures, and verifies OS disk launch. It lets users cryptographically verify OS disk root or system partition contents before processing private workloads. Sign up for the OS disk integrity tool preview now.
Experience Azure and Intel’s power
Read Azure secret computing and Intel technology case studies.
Azure secret computing with Intel SGX and Intel TDX is helping Fireblocks advance asset tokenization.
Even as cookies disappear, Decentriq is helping retailers use confidential computing in data clean rooms to better customer targeting and marketing with first-party data.

[…] must remember that data fuels AI as Microsoft enter the AI era. This explains why Microsoft want Azure to be the best data destination. Customers […]
[…] agreement between Microsoft and Dropbox has been disclosed. Microsoft is a major worldwide brand in the gaming, creativity, and […]
[…] gives customers discounts on their cloud infrastructure after meeting spending thresholds. Microsoft assists its customers in accomplishing more by automatically counting eligible marketplace […]
[…] should be noted that some browsers, such as Microsoft Edge and Google Chrome, require an additional step in order to activate the feature for playing videos in […]