Google goal at Google Cloud is to change cybersecurity for businesses by using their cutting-edge knowledge, experience, and inventive AI solutions. Nowhere is this more necessary than in security operations (SecOps), where overworked and underfunded security teams have to fight against a threat environment that is expanding in number and complexity, often using technologies that were created in the pre-cloud era.
Chronicle Security Operations platform
Google have reexamined what threat detection, investigation, and response (TDIR) with Chronicle Security Operations can be because we think that effectively defending against new threats demands modern thinking and modern solutions. We are pleased to announce Chronicle’s most recent update, which unifies our SOAR and SIEM solutions, integrates attack surface management technology from Mandiant, and offers more robust application of threat intelligence to help defenders stay ahead of the most recent threats. This announcement follows those we made about Duet AI and threat-hunting at Google Cloud Next.
“The Chronicle SecOps platform is tightly connected with Google cutting-edge threat intelligence capabilities. Bashar Abouseido, CISO, Charles Schwab, stated, “Google enjoy the orchestration features that allow us to enhance the data and bring extra context to it, so their SOC and analysts are able to prioritize that work and react with the care that is required. “We see Google as a crucial partner who will help us bring about quite a bit of advantage in the fight thatGoogle have against the kind of threats that we deal with that continue to expand on a regular basis,” the company said.
An integrated cloud-based platform
With the help of Chronicle Security Operations, businesses can store and process unfiltered data at Google size and speed, allowing security teams to identify and look into problems more swiftly. We understand that companies need to do more than simply gather data to stay ahead of threats since it might take security teams too long to uncover the information that’s really important or there are gaps in the information that is accessible for them to search and analyze.
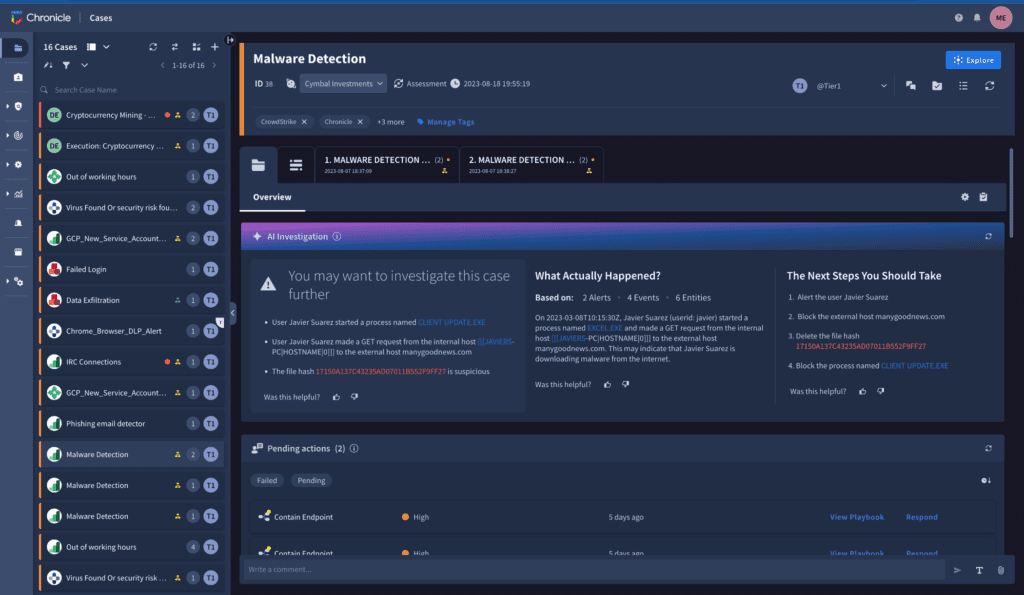
For a more streamlined and integrated TDIR experience, we can now give rich context and simple pivoting between alarms, cases, investigations, and playbooks in a single console thanks to our new consolidated interface for Chronicle SIEM and Chronicle SOAR. Every alert in Chronicle SecOps is now categorized into a case in order to aggregate similar alarms and provide security teams access to pertinent data to aid with making choices more quickly.
Using threat intelligence to proactively identify threats
A contemporary security operations platform must have a thorough grasp of the most recent risks and the capability to apply this information to each customer’s particular environment in order to protect against current attacks.
To help SecOps teams be more proactive and stay ahead of possible threats, we are enhancing Chronicle Security Operations with even more robust capabilities and risk-based outcomes. In order to reduce blind spots and ultimately increase threat detection, our new Applied Threat Intelligence, which is currently in preview, makes use of Chronicle’s scalability to automatically enrich and contextualize each event with the most recent, industry-leading threat intelligence from Google Cloud, Mandiant, and VirusTotal.
It makes use of AI and machine learning to rank risks according to each customer’s particular environment, which may assist security teams in concentrating on the most pressing dangers. A threat actor, threat campaign, or malware family association that may be utilized for custom searches or detections will be added to any relevant event in Chronicle SecOps that matches a danger indication.
Additionally, we have enabled direct viewing of breach analytics results in the Chronicle SecOps platform. Breach analytics analyzes client data from Chronicle SecOps in real-time and immediately alerts them to any new or unique attacker strategies identified by Mandiant Incident Response engagements. This makes it possible for enterprises to respond proactively in close to real-time and lessen the effects of a breach. The public preview version of Chronicle SecOps’ breach analytics is now accessible.
clients may continually detect and verify vulnerable entry points into their company with the help of our integration with Mandiant Attack Surface Management (ASM), which is now broadly accessible to all Chronicle SecOps clients. The SecOps team may prioritize investigation and remediation activities based on the exposures that have the greatest potential effect by integrating ASM to assist correlate and enrich investigations with context and a knowledge of business risk.
Increased productivity using AI
Chronicle Security Operations may free security teams from the labor caused by complicated, dispersed instruments, ushering in a new age of productivity. Duet AI in Chronicle SecOps can help transform threat detection, investigation, and response for cyber defenders by streamlining search, complex data analysis, and threat detection engineering. This can help decrease labor and increase the effectiveness of each defender by leveraging Google’s ongoing innovations in generative AI and security-specific foundation models.
With the help of Duet AI, Chronicle SecOps can automatically deliver a concise description of what is occurring in instances, provide context and advice on significant dangers, and make suggestions for how to react. The new natural language search in Chronicle is likewise powered by Duet AI. Defenders may ask inquiries using natural language, and Chronicle SecOps will construct a search query from that statement, give a fully mapped syntax, and let you to easily refine and iterate on results.
Although AI offers tremendous potential for talent advancement, we recognize that many firms will still need assistance with highly specialized skill sets. Mandiant Hunt for Chronicle, which may provide ongoing threat hunting by Mandiant professionals, was just recently added, as we previously revealed.
It combines strong Chronicle’s ability to swiftly analyze and search security data with the most recent insights about attacker activity from Mandiant’s frontline analysts. Organizations can fill the skills gap and get elite-level assistance with Mandiant Hunt for Chronicle SecOps without having to worry about recruiting, equipping, or training new employees.
Purple teaming and cyberdefense transformation are just two of the many Chronicle-ready services that Mandiant provides to help clients before, during, and after a cyber disaster.
Google were pleased about the results that the new capabilities in the integrated Chronicle Security Operations platform may assist cyber security teams in any business produce.


[…] National Cyber Security Centre (NCSC), a pioneer in cyber security recommendations and guidelines, particularly those pertaining to secure cloud adoption, is […]
[…] using the most recent browsers and technological advancements and maintaining the robustness, security, and usability of your app. With the stress of overseeing a complicated test infrastructure gone, […]
[…] for a vendor’s preferred platform does not apply to them, according to Craig Robinson, VP of Security Services at IDC Research. “Services like IBM’s Threat Detection and Response offering […]
[…] procedure in place. Maintaining a company’s security is not just the responsibility of the IT, security, and chief information security officer (CISO). Every employee at a firm has to get training and be […]