The Iranian government-backed threat actor APT42 and their focused phishing activities targeting Israel and Israeli targets are the subject of today’s insight sharing from Google’s Threat Analysis Group (TAG). Additionally, Google is verifying recent accusations that APT42 has been targeting accounts related to the US presidential election.
APT42, which is linked to Iran’s Islamic Revolutionary Guard Corps (IRGC), frequently targets prominent users in Israel and the United States, such as political campaigns, diplomats, think tank employees, and members of NGOs and academic institutions that participate in discussions about foreign policy.
About 60% of the known geographic targets of APT42 over the last six months have been in the United States and Israel, including former senior Israeli military officers and people connected to both U.S. presidential campaigns. The aforementioned efforts showcase the group’s proactive and diverse approach to promptly modify its operational focus to align with Iran’s military and political agenda.
Spikes in APT42 targeting against Israel
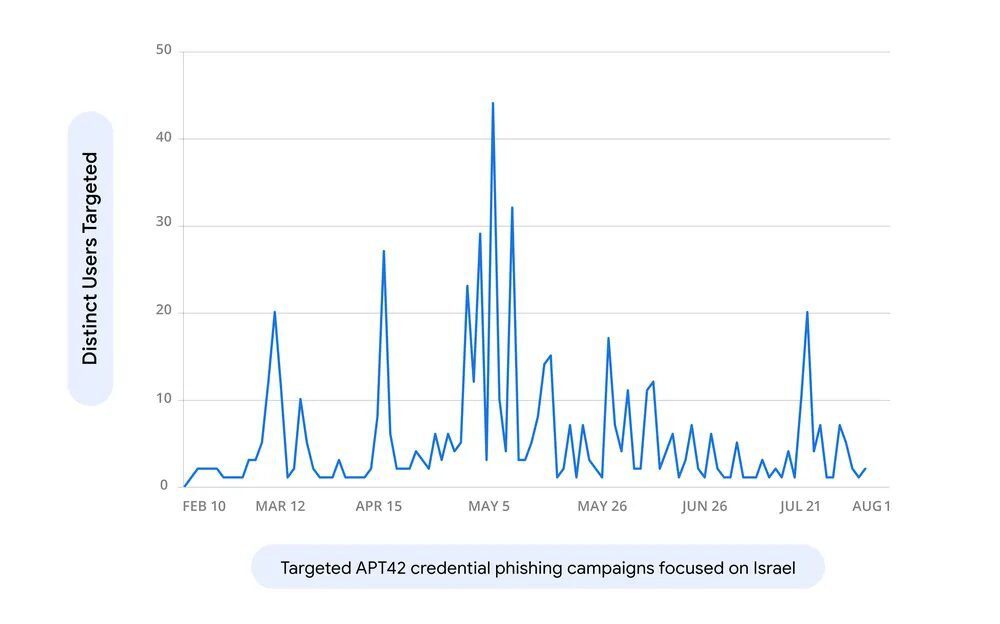
APT42 stepped up its targeting of Israeli consumers in April 2024. They went after academics, NGOs, diplomats, and anyone with ties to the Israeli military and defence establishment.
In their email phishing efforts, APT42 employs a range of strategies, such as hosting malware, creating phishing pages, and using malicious redirects. For these reasons, they typically attempt to misuse services provided by Google (including Sites, Drive, Gmail, and others), Dropbox, OneDrive, and others. TAG destroyed APT42’s infrastructure by resetting any hacked accounts, notifying targeted users of government-backed attacker warnings, updating detections, blocking malicious Google Sites pages, and adding malicious domains and URLs to the Safe Browsing blocklist.
Phishing on Google Sites: Google removed several Google Sites set up by APT42 that purported to be a petition from the authentic Jewish Agency for Israel, urging the Israeli government to mediate a resolution to the conflict. Rather than being in HTML, the petition’s text was embedded in picture files. The Sites page had a ngrok redirect URL, a free service for developers that APT42 has previously used to route people to phishing pages.
Targeting military, defense, diplomats, academics, and civil society: APT42 sought to employ social engineering to target former senior Israeli military officers and an aerospace CEO by posing as a journalist and soliciting comments on the recent air strikes. The targets included the military, defence, academia, and civil society.
Additionally, they sent emails with social engineering to academics, NGOs, political organisations, and Israeli embassies. The emails didn’t contain any malicious material, and they were sent from accounts housed by different email service providers. Before APT42 made an attempt to compromise the targets, these emails most likely intended to stimulate response from the recipients. Google suspended Gmail accounts that were linked to APT42.
A phishing kit landing page that harvested Google login credentials was the destination of a shortened URL link found in a benign PDF email attachment sent as part of a June 2024 campaign that targeted Israeli NGOs. The email attachment was disguised as part of the official Project Aladdin.
Targeted credential phishing: APT42 relies heavily on social engineering to provide the impression that they are more credible to their targets, which contributes to their effectiveness in this tactic. They frequently set up accounts or domains that mimic businesses that the target may find interesting. As an illustration:
- Since April 2024, APT42 has waged several campaigns in the guise of the official Washington Institute for Near East Policy, targeting Israeli journalists and diplomats as well as scholars at American think tanks. Attackers used the Washington Institute as the real researcher’s email display name in these attacks, but the underlying email address was not from the official.org domain.
- Typosquat domains that are extremely similar to the real domains of the companies they pretend to be are registered by APT42. For instance, APT42 impersonated the real Institute for the Study of War and targeted US military personnel under the domain understandingthewar[.]org. In a similar vein, APT42 set up brookings[.]email in order to impersonate the Brookings Institution and utilised it in several activities directed at Israel.
Focusing on those involved in the US presidential election
Google has spent many years trying to detect and stop unwanted activities during democratic elections. Google interfered with APT42 attempts to target accounts connected to the Trump and Biden presidential campaigns in the 2020 U.S. presidential election cycle.
During the current U.S. presidential election cycle, TAG discovered and stopped a tiny but consistent pattern of phishing attempts using APT42’s Cluster C credential. APT42 targets in May and June comprised the personal email accounts of about twelve people connected to both President Biden and former President Trump, including persons connected to both campaigns and current and former U.S. government officials. Google stopped multiple APT42 attempts to access the targeted people’s personal email accounts.
According to recent public reports, APT42 has been successful in breaching accounts with a number of different email providers. Google noticed that the gang was able to effectively access a prominent political consultant’s personal Gmail account. Apart from their customary measures of promptly safeguarding any compromised account and dispatching government-endorsed attacker alerts to the targeted accounts, Google notified law enforcement of this hostile behaviour in early July and are still collaborating with them.
Google also alerted campaign officials to the increased malicious activity that Google was observing, which was coming from foreign state actors, and Google emphasized the need for improved account security measures on individual email accounts.
TAG is still monitoring failed attempts by APT42 to access the personal accounts of people connected to President Biden, Vice President Harris, and former President Trump; these people include campaign staff members and present and past government officials.
Recognizing the customized credential phishing used by APT42
APT42 frequently employs strategies like delivering phishing links either directly in the email body or as a link in an otherwise innocent PDF attachment in phishing campaigns that TAG has disrupted. Under such circumstances, APT42 would use social engineering to entice its victim into scheduling a video conference. After that, the link would take the target to a landing page where they would be asked to log in and directed to a phishing page.
In one campaign, the target was sent to a phoney Google Meet destination page using a phishing lure with an attacker-controlled Google Sites link. Dropbox, Skype, and OneDrive were some more enticements. Google has methodically prevented these attackers from abusing Google Sites in over 50 comparable attacks over the past six months.
Sending authentic PDF attachments as part of a social engineering enticement to foster trust and persuade the target to interact on other platforms like Signal, Telegram, or WhatsApp is another APT42 campaign template. Google anticipate that after using these sites, the attackers will deploy a phishing kit to obtain passwords.
Several phishing kits from APT42 target different sign-on pages, such as:
- GCollection/LCollection/YCollection: a highly developed credential harvesting program that TAG has seen in action. It can collect credentials from users of Google, Hotmail, and Yahoo, in that order. Since APT42 was first detected using this kit in January 2023, it has undergone continuous improvement. The most recent version offers a smooth flow that works with all three platforms and supports device PINs, one-time recovery codes, and multi-factor authentication. Together with the signs of compromise, a collection of landing page URLs are provided.
- DWP is a less feature-rich browser-in-the-browser phishing kit that is frequently distributed through URL shortening services than GCollection.
Reconnaissance is used to help spear phishing by locating personal email addresses that may not have multi-factor authentication or other security features that are often found on corporate accounts. This is done utilising open-source marketing and social media research tools.
In order to more effectively target their initial phishing attempts, APT42 has also developed a thorough understanding of the email providers they target. They frequently use failed login or recovery workflows to investigate the security settings of the accounts they target in order to identify the configured second factor for authentication.
For instance, they have introduced support for Device Prompts in their GCollection phishing kit and in certain circumstances, they have discovered that an account is set up to use them as an acceptable second factor. The target’s current geographic location is then combined with this method by APT42 using social engineering or public research data. Because of this, efforts to log into and recover from APT42 frequently come from the right place, using the right credentials, and using the right second factor to authenticate the user.
Once APT42 has access to an account, they frequently add more ways to get in, such as altering recovery email addresses and using features that let them use apps that don’t support multi-factor authentication, like third-party app passwords on Yahoo and application-specific passwords on Gmail. Users are shielded against this approach by Google’s Advanced Protection Program, which disables and revokes these application-specific passwords in Gmail.
In summary
The Google Threat Intelligence Group, which includes Mandiant and TAG, assists in identifying, tracking, and mitigating risks. These threats can range from cyber espionage campaigns against high-risk businesses to coordinated influence operations. Over 270 government-backed attacker groups from more than 50 countries are being tracked and disrupted by TAG, and Google is frequently publish their findings to keep the public aware about these risks.
As previously said, APT42 is a highly skilled and tenacious threat actor that doesn’t seem to be giving up on its attempts to target people and apply cutting-edge strategies. They have demonstrated the capacity to conduct many concurrent phishing efforts during spring and summer, with a special emphasis on Israel and the United States. Google can anticipate more APT42 campaigns in Iran as hostilities between Iran and Israel heat up.
Google is also continue to be on the lookout for potential targets throughout the US election season, and Google strongly advise anybody who may be considered high-risk, including as government officials, elected officials, candidates, campaign staff, journalists, and others, to enrol in Google’s Advanced Protection Program. The purpose of APP, a free opt-in tool, is to safeguard specific users from these kinds of attacks by prohibiting unauthorized persons from accessing accounts even when they are aware of the password.

