IBM Storage Defender
With IBM FlashSystem and IBM Storage Defender, you can increase the effectiveness of your defences against cyberattacks.
Cybercrime is profitable these days. It occurs as a result of the minimal risks and great returns. Cybercrime is steadily rising instead than abating. In 2023, the FBI received a whopping 880,418 complaints containing potential damages in excess of USD 12.5 billion. The number of complaints has climbed by around 10% compared to 2022, while damages have risen by about 22%.
Ransomware assaults have been recognized as the most widespread threat worldwide since the 2024 IBM X-Force Threat Intelligence Index. Cybersecurity has become the most expensive investment in commercial technology right now, which is not unexpected considering the disastrous effects of ransomware and the efforts companies have taken to defend themselves against it.
The ransomware code collects data about target networks and important resources, including databases, important files, snapshots, and backups, when a hack occurs. With little action, the threat may infect hourly, daily, and monthly complete backups while going dormant for weeks or months. The ransomware starts the real assault by encrypting and rendering important files and databases useless when it has gathered all the data it need. Due to the speed of file encryption, an assault may severely damage vital corporate data in a matter of minutes.
Elevate the degree of data resiliency
Thankfully, it is possible to identify ransomware attacks and establish many preventative measures beforehand in order to limit and manage the danger. IBM offers end-to-end data resilience solutions to effectively protect organizations against ransomware and other malware threats. These solutions assist organizations deal with the many types and techniques used to carry out an attack.
Logically separated from production settings, immutable copies of data serve as the foundation for storage protection offered by IBM Storage FlashSystem. Ransomware attacks, malevolent acts, or human mistake cannot alter or remove these Safeguarded Copies. Through its new Flash Core Modules 4 (FCM4), which continually monitor statistics acquired from every single I/O using machine learning models to early identify abnormalities at block level, IBM Storage FlashSystem now provides inline data corruption detection.
IBM Storage Defender, on the other hand, is an end-to-end solution designed specifically to streamline and coordinate business recovery procedures by providing a consolidated picture of data protection and cyber resilience status across the hybrid cloud and integrating easily into security dashboards. It uses AI-powered sensors to quickly identify irregularities in databases, file systems, virtual machines (VMs), and other applications that are hosted in Linux VMs.
Better in tandem
Within the cyber resilience sector, these IBM Storage solutions are industry leaders. When combined, their complementary skills may significantly increase the capacity for early threat detection, data protection, and quick recovery. The following explains how they coordinate their interactions:
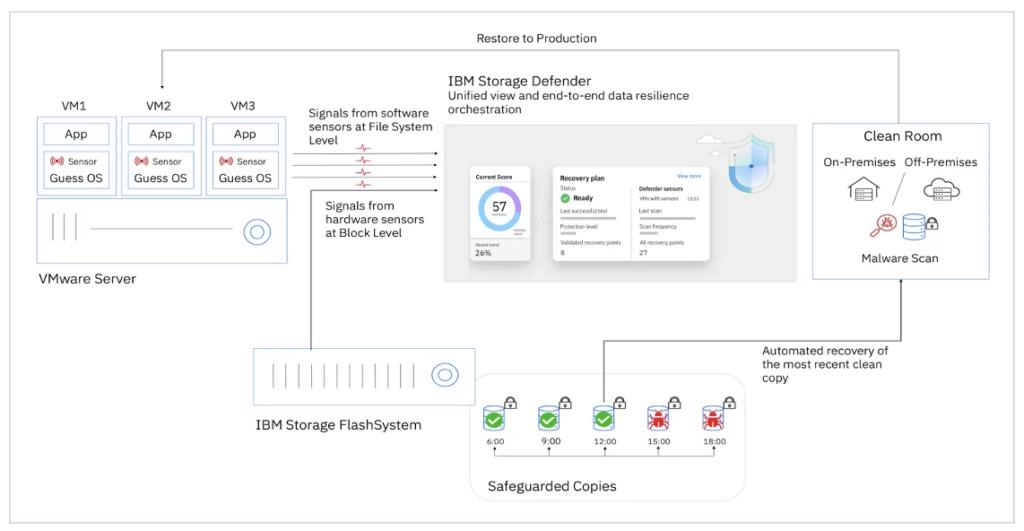
IBM Storage Defender uses a combination of its software sensors and the inline data corruption detection (IDCD) from the IBM FlashSystem Flash Core Modules to enhance threat detection. With more data from this dual source, the machine learning models are able to provide more accurate findings and fewer false positives.
Furthermore, IBM Storage Defender may assist customers in expediting the restoration of production systems by pinpointing the location of the most recent reliable copy. Both conventional backups and main storage may include these encrypted copies. Instead of waiting for restoration across the network, the client may use the value of the main storage if the copy is offered there to resume activities in a matter of minutes.
Workloads may be restored in a separate “Clean Room” environment as an extra measure of security so they can be examined and verified before being recovered to production systems. Clients may be assured that the data is clean and that business activities can be securely resumed thanks to this verification. Environments for clean rooms may be set up by seamlessly integrating partner solutions.
IBM Storage FlashSystem
Benefits to business
The following advantages are brought about by the combined activity of IBM Storage Defender and IBM Storage FlashSystem, which strengthens the defences against ransomware:
- A consolidated and transparent picture of the entire state of data resilience for both main and secondary storage.
- Automatic generation of Safeguarded Copies, which are conceptually separated from production environments and are impervious to deletion or modification in the event of a ransomware attack.
- Block-level ransomware detection in 60 seconds or less.
- A thorough description of the location and validation status of Safeguarded Copies, allowing for their rapid recovery as a reliable source of data.
- The capacity to restore a Safeguarded Copy in no more than 60 seconds.
- To ensure that workloads can be safely returned to production, use a clean room environment.
- Notifications to incident teams and the Security Operations Centre (SOC) to assist in coordinating the implementation of recovery strategies.
As of right now, only IBM offers complete data resilience across the hybrid cloud. In order to maximize business continuity in the face of ransomware attacks and other data loss concerns, IBM is still committed to enhancing the synergistic capabilities of IBM Storage Defender and IBM Storage FlashSystem.
