DDoS Attack
Distributed Denial of Service (DDoS) attacks overload a server, service, or network with internet traffic from several sources. A “botnet,” or network of compromised computers or devices, controlled by the attacker, executes these attacks.
DDoS attacks aim to make the targeted system or network inaccessible to users to inflict downtime, financial losses, and reputation damage. Amplification attacks, SYN floods, and HTTP floods generate huge traffic and drain the target’s resources.
Azure DDoS Protection
What is DDoS Protection in Azure?
DDoS attacks are a major availability and security risk for cloud app users. DDoS attacks drain an application’s resources, preventing permitted users from accessing it. DDoS assaults can target any public internet endpoint.
When combined with application architectural best practices, Azure DDoS Protection improves DDoS mitigation. It is automatically adjusted to help safeguard your particular Azure resources within a virtual network. Enabling protection on a virtual network, whether new or old, is easy and doesn’t involve any changes to applications or resources.
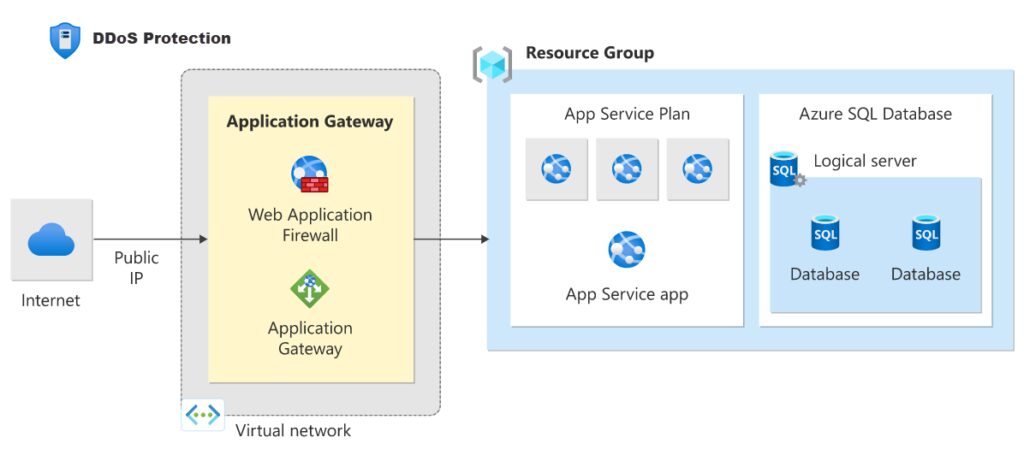
Azure DDoS Protection
Layer 3 and layer 4 network layers are protected by Azure DDoS Protection. Using a WAF offering, you must implement protection at the application layer in order to secure web applications at layer 7.
The tiers
DDoS Network Protection
To prevent DDoS assaults, Azure DDoS Network Protection offers improved DDoS mitigation technologies in conjunction with best practices for application architecture. It is automatically adjusted to help safeguard your particular Azure resources within a virtual network.
DDoS IP Protection
One pay-per-protected IP model is DDoS IP Protection. The following value-added services set DDoS IP Protection apart from DDoS Network Protection: cost protection, discounts on WAF, and support for DDoS rapid response.
Crucial elements
- Always-on traffic monitoring: Your application’s traffic patterns are watched around-the-clock to check for signs of DDoS assaults. As soon as the attack is identified, Azure DDoS Protection immediately and automatically neutralises it.
- Adaptive real time tuning: Intelligent traffic profiling chooses and modifies the profile that is most suited for your service based on the traffic flowing through your application over time. Over time, the profile is modified to reflect variations in traffic.
- Analytics, metrics, and alerts for DDoS protection: For each public IP address of the protected resource in the virtual network with DDoS enabled, Azure DDoS Protection applies three automatically adjusted mitigation strategies (TCP SYN, TCP, and UDP). Machine learning-based network traffic profiling is used to automatically configure the policy thresholds. Only when the policy threshold is surpassed does DDoS mitigation take place for the attacked IP address.
- assault analytics: Obtain comprehensive summaries following an assault, as well as in-depth reports in five-minute intervals throughout the attack. For near real-time monitoring during an attack, stream mitigation flow logs to an offline security information and event management (SIEM) system or Microsoft Sentinel.
- Assault metrics: Azure Monitor provides a summary of the metrics from each assault.
- Attack alerting: By utilising integrated attack metrics, alerts may be set up to sound both at the beginning and end of an attack as well as throughout its length. Alerts are integrated with your operational software, such as the Azure interface, Splunk, Azure Storage, Microsoft Azure Monitor logs, and email.
- assault analytics: Obtain comprehensive summaries following an assault, as well as in-depth reports in five-minute intervals throughout the attack. For near real-time monitoring during an attack, stream mitigation flow logs to an offline security information and event management (SIEM) system or Microsoft Sentinel.
- The Azure DDoS Rapid Response (DRR) team is available to clients with Azure DDoS Network Protection enabled during an active assault. They can assist with attack investigation during an attack and post-attack analysis.
- Azure has native platform integration. includes setting up the Azure portal. Azure DDoS Protection is aware of your resources and how they are set up.
- Turnkey protection: Once DDoS Network Protection is activated, all resources on a virtual network are instantly protected by simplified configuration. Neither user definition nor intervention is necessary. Likewise, when DDoS IP Protection is activated for a public IP resource, its simple configuration instantly protects it.
- Multi-layered security: Azure DDoS security offers protection at the network layer (Layer 3 and 4; provided by Azure DDoS Protection) and at the application layer (Layer 7, provided by a WAF) when used in conjunction with a web application firewall (WAF). Third-party web application firewalls that are offered in the Azure Marketplace and Azure Application Gateway WAF SKU are examples of WAF products.
- Broad mitigation scope: To defend against the most powerful DDoS attacks, all L3/L4 attack pathways can be neutralised with worldwide capacity.
- Cost assurance: Get credit for application scale-out and data-transfer services for resource expenses brought on by known DDoS attacks.
Architecture
Azure DDoS Protection is intended for services that are set up within a virtual network. The standard infrastructure-level DDoS defence, which guards against frequent network-layer attacks, is applicable to different services.
Azure DDoS Protection cost
There’s no need to develop different DDoS protection plans because a single DDoS protection plan can be deployed across numerous subscriptions under a tenant for DDoS Network Protection. There is no need to develop a DDoS protection strategy for DDoS IP Protection. On any public IP resource, users can activate DDoS IP protection. See Azure DDoS Protection price to find out more about Azure DDoS Protection costs.
Best Practices
Utilise these recommended practices to increase the efficacy of your DDoS mitigation and protection strategy:
- Design infrastructure and applications with redundancy and resilience.
- Protect data, apps, and networks with multi-layered security.
- To guarantee a coordinated reaction to DDoS attacks, create an incident response strategy.
