In this article, we will learn how to use Google Cloud networking and network security to defend your website against DDoS attacks.
Google Cloud makes large investments in its capabilities and is always innovating to prevent cyberattacks like distributed denial-of-service attacks from bringing down websites, apps, and services. It’s crucial to safeguarding its clients.
Google Cloud networking and network security
Google Cloud uses parts of its Cloud Armor, Cloud CDN, and Load Balancing services in its Project Shield offering, which leverages Google Cloud networking and its Global Front End infrastructure to help defend against attacks, including stopping one of the largest distributed denial-of-service (DDoS) attacks to date. It integrates them into a strong defense architecture that can assist in maintaining important websites of public interest online despite ongoing attacks.
Enterprise clients can also benefit from Google Cloud networking and network security, even though Project Shield is intended for users who are particularly vulnerable to DDoS attacks, such as news organizations, infrastructure supporting elections and voting, and human rights organizations. Using the same defense infrastructure as Project Shield, Google Cloud can assist you in safeguarding workloads anywhere on the web for your application, website, or API. This is the method.
Distributed Denial-of-Service attacks
DDoS is a severe threat that can bring your service offline without the need for specific permissions or security breaches. These attacks are difficult to trace and could originate from anywhere in the world. They commonly employ infected machines (and occasionally light bulbs) as part of botnets. The attacks resemble typical network traffic, but they happen extremely quickly hundreds of millions of fraudulent requests are sent per second.
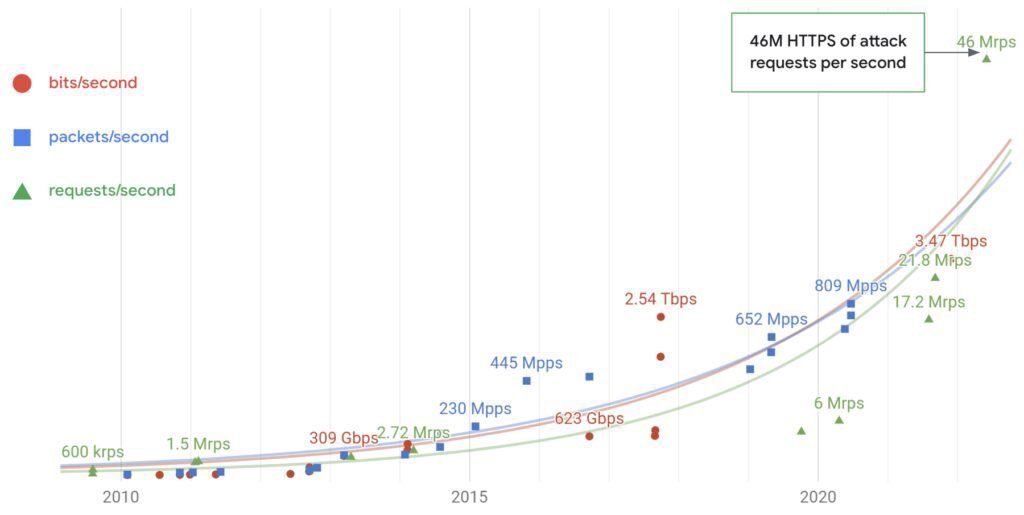
You must distinguish between valid and malicious traffic in order to protect your service; nevertheless, you must nonetheless process all requests, regardless of where they come from. Rather than attempting to stop the request escalation, Google wants you to be free to concentrate on providing value to your audience. Effective defenses must be able to scale up to handle more traffic than you actually receive in order to accomplish this.
How to begin
With time, older defensive strategies have been shown to be insufficient. Requests that appear to be coming from reputable sources are difficult for firewalls to deny. Investing heavily in infrastructure is necessary for traffic filtering, which is costly and uses resources that may be better utilized.
Using the networking and network security services provided by Google Cloud, protecting your website only takes a few minutes. With the use of its most recent machine learning (ML)-based defenses, its solutions can neutralize threats and cache your material to speed up user delivery while lessening the strain on your hosting servers. Although you can host your material anywhere, Google Cloud’s Cloud Armor, material Delivery Network, Load Balancer, and possibly Adaptive Protection will be used to safeguard it.
You can configure these safeguards for your company in two different ways. You have two options: use the Google Cloud console interface to follow its instructions below, or run this Terraform script (with a few tweaks.)
The Google Cloud console interface can be used to safeguard your service in the following step-by-step manner:
- Take up a Google Cloud project first.
- You can use the same project again if Google Cloud is already hosting your material.
- It is necessary to activate APIs for:
- Cloud Load Balancer
- Cloud CDN
- Cloud Armor
- To locate your material, make a network endpoint group, which is a basic proxy. There are various forms for you to complete.
- Give it a name.
- ‘New network endpoint’ gives you the option to point to either an IP address or a fully qualified domain name.
- Here, use the IP address and port of your website (instead of 8.8.8.8). This stage instructs the load balancer on where to retrieve material in response to incoming requests.
- Press the Create button.
- You can click Next four times to construct a new load balancer (global front end) with the following configurations, all of which are defaults:
- Application load balancer
- Public facing (external)
- Best for global workloads
- Global external Application Load Balancer
- Assign a name to the load balancer.
- Indicate the direction of the traffic.
- Choose Create IP Address after naming the frontend (it’s no more expensive than Ephemeral and lets you direct traffic to it regularly).
- For your Frontend Load Balancer arrangement, which will resemble slide (2), use that IP.
- Add the Backend service after that.
- Then select “Create a Backend Service.”
- Give it a name.
- Select the Internet network endpoint group as the backend type. The information that the load balancer needs to establish a connection to a place on the internet is stored in this container.
- Click ‘New Backend’ to get a list of network endpoint groups, of which the group we created above ought to appear. Select that.
- We will require Enable Cloud CDN later, so make sure it is checked, as it should be.
- The cache mode settings work well. Cache static content refers to the fact that Cloud CDN will obey cache-control headers and cache static content (such images and PDFs) in the absence of an explicit cache-control header.
- You can return later to change Cloud Armor rules in that UI, leaving Security settings as they are.
- If you need to protect your backends from particular sources (such known attackers, certain geographic areas, and large volume), you can add rules to the Cloud Armor edge security policy that will take effect before traffic reaches Cloud CDN. These rules can also be added in the Cloud Armor UI at a later time.
- To complete the load balancer’s addition of the backend service, click Create.
- To configure your new load balancer, click the Create button at the bottom of the page.
- Utilizing the same static IP as your HTTP load balancer, repeat steps 4 through 7 for HTTPS.
- You can upload your own certificates or choose Google-Managed certificates. If you utilize Google-Managed certificates, provide the certificate by creating a CNAME record according to the guidelines.
- To make your defense configuration simpler, you can use the same security policy you made for your HTTP load balancer, or you can utilize a second security policy.
- You can now direct your traffic to your newly configured load balancer. Don’t forget to update your domain’s DNS settings to point to the newly established static IP.
- [Selective] A couple more clicks will grant you ML-based protections for your backend:
- Enroll in the Paygo Cloud Armor Service Tier (or use Annual to save money on an annual basis).
- Open the policies for Cloud Armor.
- Navigate to your policy by clicking.
- Select Edit.
- Select Enable under Adaptive Protection.
- Press Update.
- Select “Add rule.”
- To access evaluateAdaptiveProtectionAutoDeploy(), select Advanced Mode.
- Enter 0 to use the rule at high priority, or any other low value.)
- Press Add.
- With the knowledge it has gained about attack patterns and typical traffic, Google Cloud can now adjust to these patterns.
Enhancing the caching layer
With the cache that cloud CDN offers, traffic can resolve at the Google edge, reducing latency and providing a break for your backend. That is very easy to activate on your load balancers and helps guard against broad, shallow DDoS attacks.
Google Cloud’s cache will be directed by the cache-control headers that your backend delivers, but it can also permit default caching of static resources, like photos, even in the lack of headers. While maintaining freshness, using a short Time-To-Live (TTL) might be quite beneficial in reducing request floods. Backend overload can be avoided even if you set your TTL to “one second.”
Start now
Try this out right now by selecting a backend that would benefit from more accessibility and dependability, adding a load balancer and CDN to it, and then see as happiness increases. Protection-as-a-service, so you may concentrate more on the happiness and have less headaches.

