Cloud KMS
A cloud-based key management system called Google Cloud Key Management Service (KMS) lets you generate, utilize, and maintain cryptographic keys as well as carry out cryptographic activities safely. Your data is safeguarded both in transit and at rest thanks to its unified platform for handling encryption keys.
Advantages
Expand your security worldwide
Expand your application to take advantage of Google’s worldwide reach while delegating to Google the burden of handling important management issues, such as handling redundancy, latency, and data residency.
Assist in fulfilling your compliance obligations
Utilize software-backed encryption keys, FIPS 140-2 Level 3 verified HSMs, customer-supplied keys, or an external key manager to simply encrypt your data in the cloud.
Benefit from Google Cloud product integration
Gain access to extra security features like Google Cloud IAM and audit logs while managing the encryption of data across all Google Cloud products using customer-managed encryption keys (CMEK).
Important characteristics of Cloud KMS
Handle encryption keys centrally
Cloud-based key management that lets you handle symmetric and asymmetric cryptographic keys for your cloud services as on-premises. EC P256, EC P384, AES256, RSA 2048, RSA 3072, and RSA 4096 may be produced, used, rotated, and destroyed.
Use HSM to provide hardware key security
Host encryption keys and carry out cryptographic functions in HSMs verified to FIPS 140-2 Level 3. You can safeguard your most sensitive workloads with this fully managed solution without having to worry about the administrative burden of running an HSM cluster.
Offer EKM support for external keys
Utilize encryption keys that are kept and controlled in an external key management system to encrypt data in Google services that are integrated. You may use the cloud computing and analytics capabilities while keeping your encryption keys and data at rest separate using External Key Manager.
Be the final judge of who may access your data
Key Access Justifications enhances your control over your data significantly when used in conjunction with Cloud EKM. It’s the only solution that allows you to see each request for an encryption key along with the reason behind it and a way to accept or reject decryption inside that request. The integrity promises made by Google extend to these measures.
Cloud KMS Google Use cases
Encourage adherence to regulations
Along with Cloud HSM and Cloud EKM, Cloud KMS Google supports a variety of compliance regulations that need certain key management practices and technology. It does this in a cloud-native, scalable manner without compromising the implementation’s agility. Hardware encryption (HSM), separating keys from data (EKM), and handling keys safely Cloud KMS are all required by various standards. Key management complies with FIPS 140-2 requirements.
Utilize safe hardware to manage encryption keys
Customers may need to store their keys and conduct crypto operations on a device approved by FIPS 140-2 Level 3 if they are subject to compliance rules. Customers may satisfy their regulator’s requirements and maintain compliance in the cloud by letting their keys be stored in an HSM that has undergone FIPS validation. Customers who want a certain degree of security that their important data cannot be seen or exported by the cloud provider must also be aware of this.
Control encryption keys off-cloud

Clients that must adhere to local or regulatory security regulations must use cloud computing while keeping ownership of the encryption keys. They may still use the cloud’s computing and analytics capabilities while keeping data at rest and encryption keys separate thanks to External Key Manager. Complete transparency on who has access to the keys, when they have been used, and where they are stored is maintained throughout this process.
Important Access Reasons and EKM Data Flow
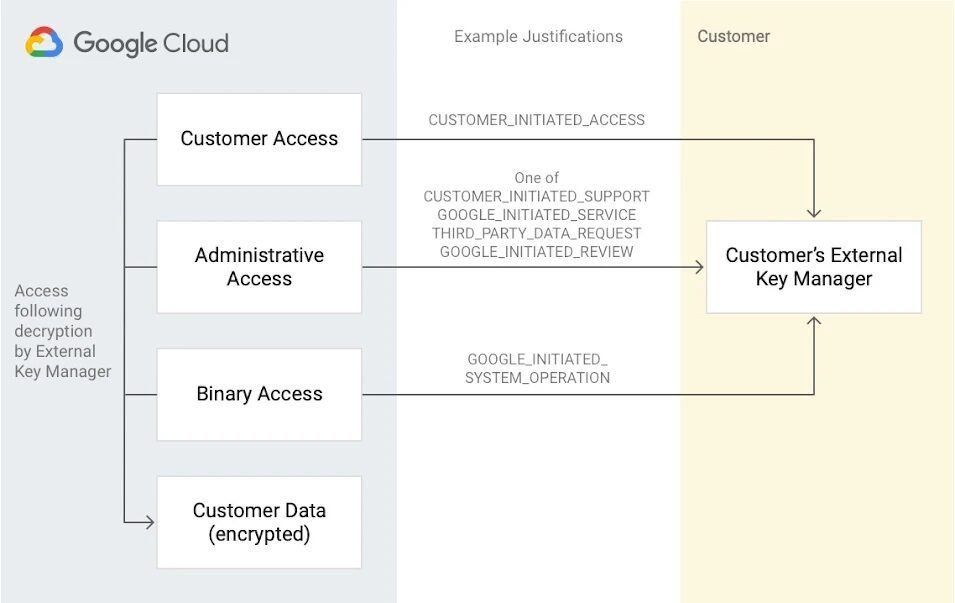
Customers of Google Cloud may see every request for an encryption key, the reasoning behind it, and a way to accept or reject decryption in relation to that request via Key Access Justifications. The use cases center on data access visibility and enforcement.
Pervasive data encryption
Using your external key management system, securely encrypt data as it is transmitted to the cloud so that only a private virtual machine VMs service is able to decode and process it.
Cloud KMS Pricing
The cost of using Cloud KMS varies according to the following products: Cloud HSM, Cloud External Key Manager, and Cloud Key Management Service.
| Product | Price (US$) |
|---|---|
| Cloud KMS: active key versions | $0.06 per month |
| Cloud KMS: key use operations (Encrypt/Decrypt) | $0.03 per 10,000 operations |
| Cloud KMS: key admin operations | free |
| Cloud HSM: key versions (AES256, RSA2048) | $1.00 per month |
| Cloud HSM: key versions (RSA 3072, RSA 4096) | 0–2,000 key versions: $2.50 per month2,001+ key versions: $1.00 per month |
| Cloud HSM: key versions (EC P256, EC P384) | 0–2,000 key versions: $2.50 per month2,001+ key versions: $1.00 per month |
| Cloud EKM: key versions | $3.00 per month |
| Cloud EKM: key use operations | $0.03 per 10,000 operations |

