Defenders must be vigilant as hacktivism rises globally
Since early 2022, Mandiant has seen hacktivist threat activities rise. This is decades after hacktivism started as an internet activism and years after many defenders last considered it a threat. This new hacktivism features a more complicated and frequently effective mix of strategies used by different actors to achieve their goals.
What is hacktivism?
The use of hacking methods to further political goals, frequently in line with social activism, is known as hacktivism. It combines the concepts activism and hacking.
Today’s hacktivists can launch massive disruptive attacks, compromise networks to leak information, conduct information operations, and even tamper with physical world processes. They have used their skills to earn fame, propagate political ideas, and assist nation-state strategic goals. Hacktivist personalities and tactics are popular among state and non-state actors seeking cyber influence due of their anonymity and versatility.
In this blog post, Mandiant analyses the hacktivism threat landscape and gives analytical tools to estimate their risk. Mandiant‘s understanding from years of observing hacktivist actors, their claims, and attacks helps organisations assess and prioritise meaningful threat activity against their networks and equities.

Defenders must monitor hacktivist threats to anticipate cyberattacks
Mandiant defines hacktivism as attacks with the avowed goal of political or social activism. The sheer size of hacktivism’s return challenges defenders to proactively sift through the noise and assess the risk posed by many actors with varying degrees of competence. Hacktivist activity is often a minor danger, but in the largest hacktivist operations Mandiant has observed, threat actors have purposefully integrated various approaches in hybrid operations to augment each other.
Nation state actors have used hacktivist techniques to assist hybrid operations that hurt victims. As volume and complexity increase and new actors use hacktivist tactics, defenders must sift, assess, and neutralise new and developing threats. Defenders benefit greatly from proactive hacktivist threat monitoring:
Monitoring hacktivism messaging and behaviour can alert defenders to sophisticated threat activity. Not only is hacktivism overt, but it also hides action from nation-states and criminals.
Hacktivism has grown in frequency and scope over the past two years, threatening several organisations. Defenders must carefully filter through trivial activity to discover meaningful targeting of their organisations and establish mitigation methods, even if most attacks have minor impacts.
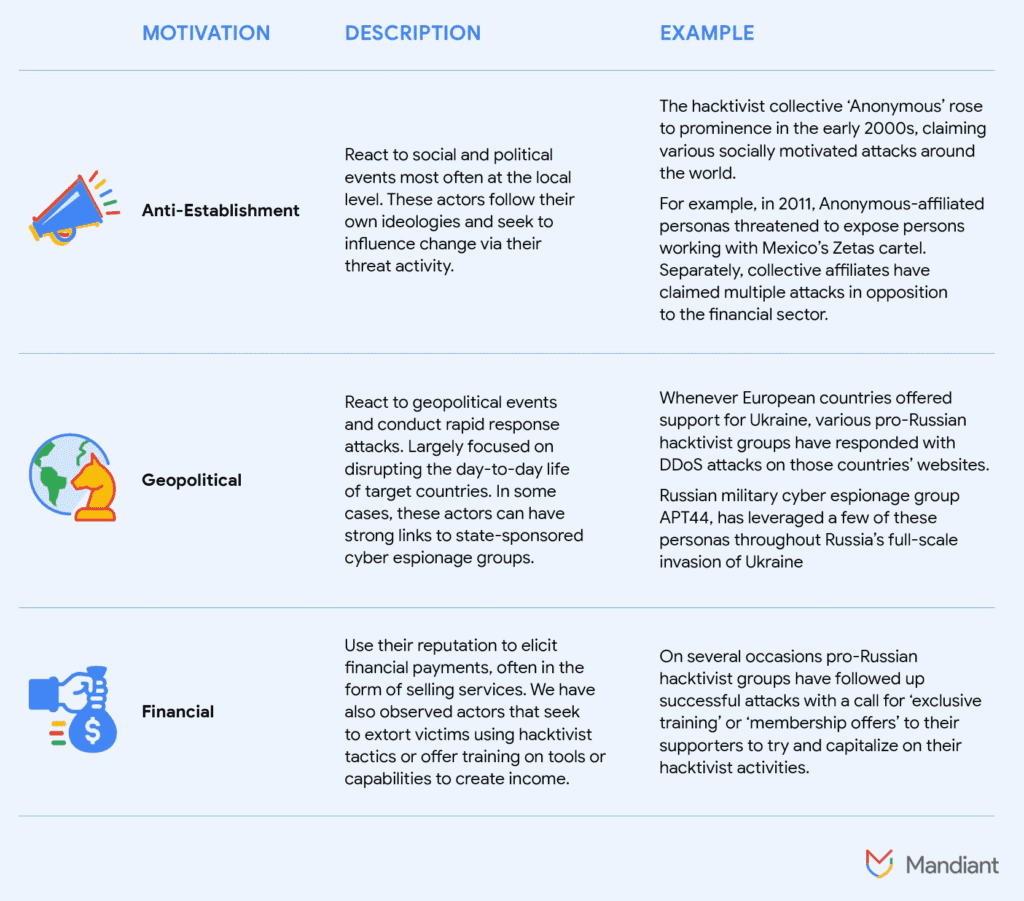
Hacktivist assaults are often inspired by global events but target organisations unrelated to the event. Targeting seemingly unrelated organisations allows players to claim greater attacks and choose high-profile targets like essential infrastructure or important enterprises to boost group prestige and notoriety.
Proactive monitoring lets defenders know when an organisation or region is at increased risk, what circumstances may precede hacktivist attacks, and when hacktivists have targeted similar industries or organisations.
In regions and industries with lesser cybersecurity maturity, networks are even more vulnerable and victims are more likely to suffer long-term consequences. In such instances, proactive monitoring helps organisations identify and mitigate imminent network dangers like other detection systems.
Scale and sophistication in the new hacktivism
A Cult of the Dead Cow hacker coined “hacktivism” in the mid-1990s. Originally, it meant “online activism,” where actors attacked victims to influence audiences and spread political or ideological views. Most hacktivist groups first claimed anti-establishment goals that endangered governments and political institutions. In the early 2010s, Anonymous-affiliated hackers attacked networks vulnerable to DDoS attacks, garnering media attention. Eventually, anti establishment hacktivism and its methods became obsolete as cybersecurity improved, networks got more resilient, and law enforcement in some places took legal action against these individuals.
After years of low intensity, low impact operations, new hacktivist groups and strategies emerged around the Russian invasion of Ukraine and the Israel-Hamas conflict. Several hacktivist groups have professed their loyalty to parties in these wars and attacked a vast range of organisations and governments. Their attacks have targeted third parties with loose associations like nationality, commercial relations, or opposing loyalty across boundaries.
New hacktivist action differs from previous activity in scale and scope of groups and activities. Some hacktivists are more adept at coordinating attacks with communications to promote their threat activities and impact audiences. Hacktivism today is not limited to low-capability actors motivated by “traditional” anti-establishment ideals. We’ve seen more geopolitically and monetarily driven entities using hacktivist facades to hide threat behaviour.
Although hacktivist activity has been used as a front for state-sponsored action for over a decade, the current level of frequency, volume, and intensity is unprecedented.
Medium Is Message: Hacktivists’ Strategic Messaging Allows Information Operations
Hacktivist attacks rely on influence and sometimes overlap with covert information operations, which use deception to manipulate information.
Strategic narrative promotion via hacktivist identities allows operators to maximise attack impact or acquire attention for their aims. Mandiant defines hacktivism as when the actor’s claims openly declare or imply political or social involvement and involve persona construction, customised message, and disruptive cyber behaviour. These strategies are crucial to hacktivism’s influence. As mentioned, hacktivism’s comeback is likely due to several variables, but its in-built mechanisms to communicate and hide identities may appeal to individuals with a variety of motivations.
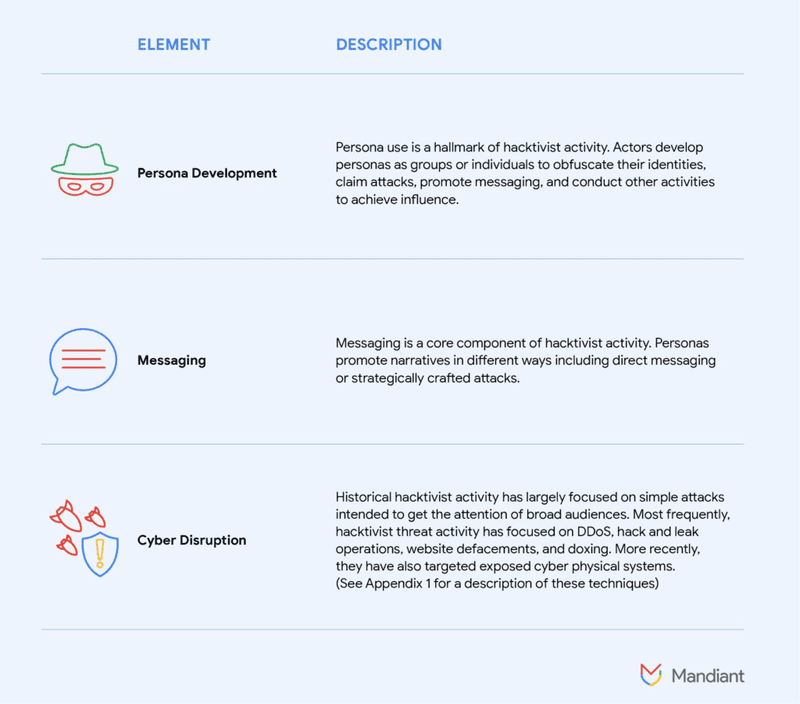
Hacktivists adopt overt personas to hide their real operators and give the sense of organic public support for a topic or event.
Hacktivist personas usually propagate their messages via direct claims or persona-affiliated online assets like social media or actor-owned sites. Distributing “tainted leaks” or running big DDoS attacks during geopolitical or cultural events can likewise incorporate meaning in the attack. Strategic targeting and other high-profile allegations help groups acquire mainstream media notice.
Hacktivist tactics incentivize actors to exaggerate their impact and make false or fabricated claims, so Mandiant advises carefully analysing groups’ messaging, claims, and any independent evidence before drawing conclusions about an actor’s motivation, capability, or efficacy. Hacktivist personalities and their acts must be analysed over time and in context of other players’ communications. Sometimes conclusive evidence is impossible.
Geopolitically motivated hackers often advance nation-state strategic goals
Given the overlap between hacktivist techniques and information operations, geopolitically driven hackers often aid nation-states achieve strategic goals. Hacktivists are usually independent, however we have found recent examples of actors with strong ties to state-sponsored cyber espionage outfits.

