What is IMDSv2?
Newly announced Amazon EC2 instance types will only utilize version 2 of the EC2 Instance Metadata Service (IMDSv2) as of mid-2024. Additionally, Amazon are implementing a number of changes to set IMDSv2 as the default option for other launch paths and AWS Management Console Quick Starts.
Framework
This service can be accessed at a fixed IP address (fd00:ec2::254 on Nitro instances or 169.254.169.254 via IPv4) from within an EC2 instance. As explained in Instance Metadata Categories, it provides you (or the code executing on the instance) with access to a multitude of static and dynamic data, such as the ID of the AMI that was used to launch the instance, block device mappings, temporary IAM credentials for roles that are associated with the instance, network interface details, user data, and much more.
According to this blog post, the v2 service employs a session-oriented mechanism whereas the v1 service uses a request/response access method. Although v2 adds further security layers to guard against four different kinds of vulnerabilities that could be used to try and get access to IMDS, both services are completely secure.
While IMDSv2 is already being used and benefiting many applications and instances, its full potential is only unlocked when IMDSv1 is turned off at the AWS account level.
Plan of Migration
With a little leeway on the 2023 and 2024 dates, these are the key actions Amazon have taken and intend to take in order to establish IMDSv2 as the standard option for new AWS infrastructure:
Amazon introduced IMDSv2 in November 2019 and demonstrated how to leverage it to provide more comprehensive defense.
In February 2020, Amazon started confirming that all recently released items from sellers on the AWS Marketplace and AWS Partners support IMDSv2.
Launched in March 2023, Amazon Linux 2023 employs IMDSv2 by default for every launch.
In September 2023, Amazon released a blog article that explains how to disable IMDSv1 throughout your AWS infrastructure and reap the complete benefits of IMDSv2.
November 2023: All console Quick Start launches will now utilize IMDSv2-only (supported by all Amazon and Partner Quick Start AMIs) as of right now. The way this is described in the EC2 Console within Additional information while starting an instance:
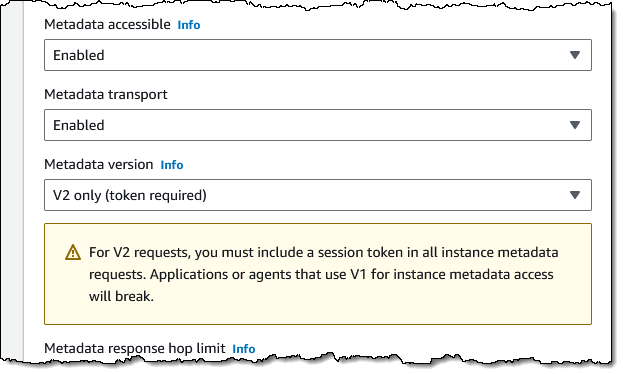
Amazon intend to provide a new API function in February 2024 that will give you the ability to manage the account-level use of IMDSv1 as the default. It is currently possible to manage the use of IMDSv1 through an IAM policy, which can restrict or remove permissions, or by using a SCP that is applied globally to an account, an organizational unit (OU), or the entire organization. IAM policies, for instance, read Work with instance metadata.
Mid-2024: By default, newly published Amazon EC2 instance types will exclusively use IMDSv2. You won’t need to restart or stop/start in order to enable/turn on IMDSv1 during or after an instance launch for transition support.
How to Proceed
Now is the perfect moment to begin your IMDSv1 to IMDSv2 conversion, following the advice in the blog post “Get the full benefits..” Along with familiarizing yourself with the suggested path on the same page, you should also become acquainted with the Tools for aiding in the transition to IMDSv2. This page not only suggests tools but also demonstrates how to create an IAM policy that prevents the use of IMDSv1 and how to utilize the MetadataNoToken CloudWatch metric to find any residual usage:
AWS re:Post: How can I utilize Systems Manager automation to enforce that only IMDSv2 is used to obtain instance metadata from my Amazon EC2 instance is another useful resource.
Amazon want you and your clients to have the smoothest transition possible.


