What is Trusted Platform Module (TPM)
A Trusted Platform Module (TPM) is a secure cryptoprocessor chip on your computer’s motherboard.
First Contact TPM for Windows
The BitLocker drive encryption, the Virtual Smart Card features, and the Crypto Provider are among the security components of the Microsoft Windows operating system that depend on TPM-based capabilities. In fact, Trusted Platform Module 2.0 needs to be activated in ALL desktop and server variants of Windows 10 and 11. By using remote attestation in conjunction with the system’s Trusted Platform Module to allow Measured Boot, the configuration of the system is protected from undetectable threats like rootkits.
On Intel’s Windows machine, Intel can quickly verify some Trusted Platform Module details by navigating to the Security Devices area of the Device Manager screen.
Now let’s engage with it. Now that a terminal window is open, let’s extract some basic system data. There are numerous powershell cmdlets available in Windows that can be used right away.
Get-Tpm retrieves the following data from the module:
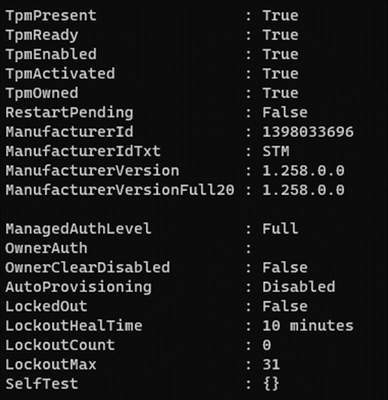
Intel can also use this information to deduce some details about the underlying system: For instance, if the platform is equipped with and employing Platform Trust Technologies (PTT), “Intel” will appear in the manufacturer section here. Here, a Trusted Platform Module from the company STM is being used.
Intel must communicate with Windows Core Security features, namely the Trusted Platform Module Base Services software component and related API, in order to utilise the Trusted Platform Module from an application standpoint. Microsoft offers tools and wrappers to facilitate the integration of these processes more quickly.
Then intel will begin examining these after that.
Linux-based TPM First Contact
Working with keys securely across any TPM 2.0 compatible module is made feasible by a set of standardised commands and libraries that enable the use of TPMs for key loading and storage in Linux.
At a high level, you can check if a TPM is present in the system by running the following command in the system log: dmesg | grep -i tpm.
Here is a step-by-step guide to several fundamental Linux system interactions:
Required conditions:
- Install a TPM 2.0 chip on the target machine.
- Install TPM 2.0 software. These packages differ per Linux distribution.The tpm2-tools and tpm2-tss packages are popular.
- Initialise TPM: Initialise the TPM before using it. Initialise the TPM with tpm2 startup.
Establish an Application Key:
- Create a key that is unique to your application and that you wish to keep in the TPM.You can use a software library like OpenSSL or a Trusted Platform Module library like tpm2-tools to generate this key.
The following is one method of generating an RSA keypair:
RSA algorithm -out appkey.pem -openssl genpkey
Fill the TPM with the Key:
- To load your application-specific key into the TPM, use the TPM 2.0 tools. For this, you’ll usually use the tpm2 load command: tpm2 load -C appkey.pub -r appkey.priv -u context.out
- This command saves the context of the key in the context.out file and loads it into the TPM. This context is necessary for using the key later on.
Apply the resident key (TPM):
- You can use this commands or libraries such as tpm2-tss to execute cryptographic operations on the TPM-resident key when your programme needs to access it. To sign data using the TPM key, for instance, run the following commands: tpm2 sign -c context.out -g sha256 -m data.txt -s signature.bin
- Using the TPM-resident key, this command signs the data and stores the signature in signature.bin.
Unload the Key (Optional):
- You can use the tpm2 flushcontext command to unload the TPM-resident key if you no longer require it: tpm2 flushcontext -c context.out.
- This releases the key’s associated TPM resources.
Shutdown and Cleanup (Optional):
- You can use the tpm2 shutdown command to terminate the Trusted Platform Module once your programme has finished utilising it.
- Analysing TPM 2.0 thoroughly Advancements in Computer Security
- Trusted Platform Module (TPM) 2.0 hardware boosts computer security. It protects your system and encryption keys as a secure cryptoprocessor.
Essential Features:
Cryptographic Key Management:
TPM 2.0 securely produces, stores, and utilises keys.Data encryption, digital signatures, and secure communication require these keys. TPM 2.0’s hardware isolation makes key theft and tampering much harder than with software-based systems.
Platform Integrity Validation:
Trusted Platform Module 2.0 monitors firmware and other critical software. It looks for any unauthorised changes that might point to malware or efforts at tampering. TPM 2.0 can protect your data by stopping the system from booting if something suspect is found.
Platform Attestation:
The firmware and software of your system can be reported on using Trusted Platform Module 2.0. Other security measures or reliable organisations can use these reports, known as attestations, to confirm the integrity of the system. This is useful for secure boot environments and for assessing a system’s health prior to allowing access to resources that are sensitive.
Benefits of TPM 2.0:
BitLocker Drive TPM 2.0 securely holds encryption keys, strengthening encryption and other functions. This makes data access tougher for unauthorised parties, even if they reach your device.
Enhanced Platform Security:
Your system will boot with authentic, unaltered firmware and software thanks to the platform integrity checks. This lessens the chance that malware will compromise your system remotely.
More Robust User Authentication:
Trusted Platform Module 2.0 can be paired with Windows Hello and other comparable technologies to provide more reliable two-factor authentication. By requiring a physical factor in addition to a password, like a fingerprint or facial recognition, this strengthens security.
TPM 2.0, Win11:
Microsoft says Windows 11 needs Trusted Platform Module 2.0. This shows how crucial hardware-based security capabilities are becoming in the battle against more complex assaults. The good news is that TPM 2.0 functionality is probably pre-installed on the majority of PCs made in the last few years. It may, however, be inactive by default in the BIOS settings.
Beyond the Fundamentals:
Flexibility:
TPM 2.0 takes a “library” approach, in contrast to its predecessor. This implies that Trusted Platform Module 2.0 features can be selected by manufacturers based on what best meets their device and security requirements. Wider acceptance across multiple platforms from laptops to embedded systems is made possible by this versatility.
Future-Proofing:
Expansion is a key design principle of TPM 2.0. As security risks evolve, it supports the installation of new functions and algorithms. This guarantees that Trusted Platform Module 2.0 will continue to be applicable and useful when new security threats arise.
