By default, Use conditional IAM and sensitive data protection to automate access control.
Recognizing the locations of sensitive data is the first step towards safeguarding it. Maintaining up-to-date knowledge of data security threats and implementing appropriate access restrictions will help you guarantee that data is utilized appropriately and with the least amount of unnecessary delay.
Google Sensitive Data Protection
Sensitive Data Protection on Google Cloud can identify sensitive data assets automatically and tag your data assets according to their sensitivity. You can allow or prohibit access to data using IAM conditions according on whether a sensitivity level tag key or tag value is present.
You can benefit from this feature:
- Based on the characteristics and categories of the data contained in those resources, automate access control across a range of supported resources. Automation makes it easier for you to manage the expansion and modifications of the data in your projects, folders, and organization.
- Limit users’ access to the supported resources, such as BigQuery, Cloud Storage, and CloudSQL, until Sensitive Data Protection has profiled and categorized them. The secure by default principle is followed by this procedure.
- When a resource’s level of data sensitivity changes, access to it is automatically changed as well.
Automated exploration and restricted entry
Sensitive data protection can search for proof of sensitive data, including financial records, medical records, secrets, and personally identifying information, among other things. Using this technology, Discovery continuously scans your data footprint for new assets and significant alterations to current assets that could raise or lower the risk to your company.
To address problems as they emerge and guarantee that your data insights are thoroughly incorporated downstream to support security workflows like data security posture management and enhance SecOps results, you can enable automated actions in addition to continuous monitoring. Sensitive data protection and Security Command Center allows you to receive vulnerability and posture notifications in the event that passwords or credentials are discovered in storage systems or when sensitive data is made publicly available.
By using conditional IAM allow and deny policies in conjunction with a new Discovery function to automatically tag your assets according to their sensitivity, you can assist avoid problems.
You can use IAM Conditions to decide whether to allow or prohibit access to principles based on whether a tag is present and/or how valuable it is. By doing this, you can make sure that access is only allowed when the person or principal requesting access has the appropriate tag attributes. You can proactively refuse access based on a tag characteristic by using reject policies.
This makes safer default settings possible, like:
- You wish to make sure that specific principals are not granted access to any of the extremely sensitive data within your organization or project.
- Your platform is receiving a lot of fresh data, therefore you want to restrict access until after it has been properly labeled and scanned.
Safer by default, automated
You may assist in automating appropriate access control with Sensitive Data Protection‘s automated data tagging and IAM conditional access.
Take a look at this instance: New BigQuery tables are created by your data team every week. A few different projects and datasets use these tables, which are shared and transferred around. You are worried that some of these assets might contain extremely sensitive customer data, like personally identifiable information (PII), or moderately sensitive data, such demographic data, but you still want to maintain business momentum by sharing these tables automatically with the larger team. Nonsensitive data can be shared with the entire team, but those two types of data should only be viewed by a limited group of team positions.
Step 1: Establish IAM Tags
Make a set of tags first to symbolize these three categories:
Level 1 : Low Sensitivity (no PII)
Level 2 : Moderate Sensitivity (names and demographic details)
Level 3 : High Sensitivity (unique or sensitive identifiers)
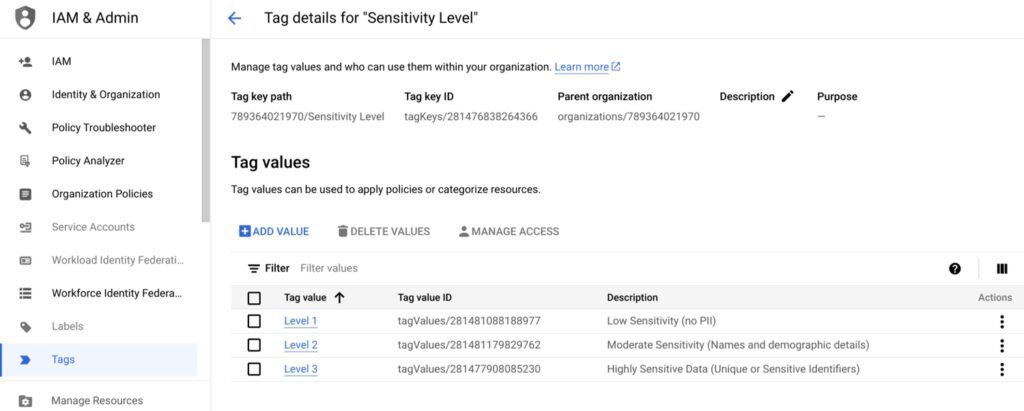
Step 2: Turn on IAM Conditional Access
As long as the data is automatically classified as “Level 1” or “Low” sensitivity data, give your data team access.
Tables that are not properly marked will no longer be accessible.
Step 3: Give “Automated Tags” permission to operate.
To map the Sensitivity Level to the relevant tag in your business, enable the “Tag resources” action in the setup of your Sensitive Data Protection discovery scan.
Now, upon creation, a table will remain inaccessible to your team until Sensitive Data Protection has automatically found, categorized, and annotated it. By putting the necessary restrictions on their IAM grants, you can make sure that only the relevant roles have access to the higher sensitive assets.
Making use of IAM Deny
Conditional IAM grants were utilized in the aforementioned scenarios to control access according to sensitivity. In certain situations, you could also wish to restrict access due to sensitivity. Think about a scenario where a partner is allowed access to particular tables for various use cases. Make sure this partner doesn’t have access to any really private information.


