Google Cloud Security Command Center
IT teams are relied upon to support cloud infrastructure security as developers employ Vertex AI, Google Cloud’s end-to-end AI platform that includes user-friendly tools to create the next generation of AI apps. In keeping with the Secure AI Framework (SAIF) that Google unveiled the previous year, they would want to disseminate methods and resources that clients may use to assist in securing AI models, goods, and technology.
Advise use Google Cloud’s Organization Policy Service first. Organization policies, which include Vertex AI-specific rules to keep developers working inside centrally-defined boundaries, set limits on how cloud resources may be configured.
Google’s integrated security and risk management tool for Google Cloud, Security Command Center Premium, now integrates with organization policies to provide near real-time detection of modifications to AI resource settings and rules, both of which have the potential to raise cloud risk. The new Security Command Center features are now accessible to most people.
Preventive and investigative mechanisms to safeguard Vertex AI applications
Google Security Command Center
Security Command Center provides visibility of AI workloads and apps without depending on point-in-time snapshots that may easily go out of date since it is integrated into the Google Cloud architecture. This is critical because workloads using AI that are hidden from view cannot be protected.
Once identified, Security Command Center applies its first-hand understanding of the architecture and operations of Vertex AI to provide posture controls that are tailored to and advised for Vertex AI workloads.
The new features of Security Command Center include pre-built security controls that can be activated with a single click, in contrast to older cloud security solutions that often handle AI applications like any other workload. It provides ongoing monitoring to identify instances in which security rules are broken by Vertex AI resource setups. Then, when the setup of the core AI infrastructure deviates from security best practices, for example, when:
- Recently developed Vertex AI Access to workbench notebooks is possible via public IP addresses.
- File download functions are enabled by Workbench instances.
- Workload access rights for Vertex AI are modified.
Additionally, Security Command Center alerts security managers to policy modifications, enabling teams to promptly ascertain if posture controls have been eased as a result of malicious intent or policy misconfiguration. In order to find common misconfigurations and vulnerabilities across different services required by AI workloads, such as computing, storage, and networking, it also offers Security Health Analytics (SHA).
AI workloads may benefit from defense-in-depth security when proactive posture settings are combined with near real-time detection in a single solution. The Security Command Center UI has a dedicated card that highlights pertinent security discoveries, making it simpler to enhance the security of Vertex AI implementations. Security teams may monitor their risk posture with the use of this quick overview of the AI security status.
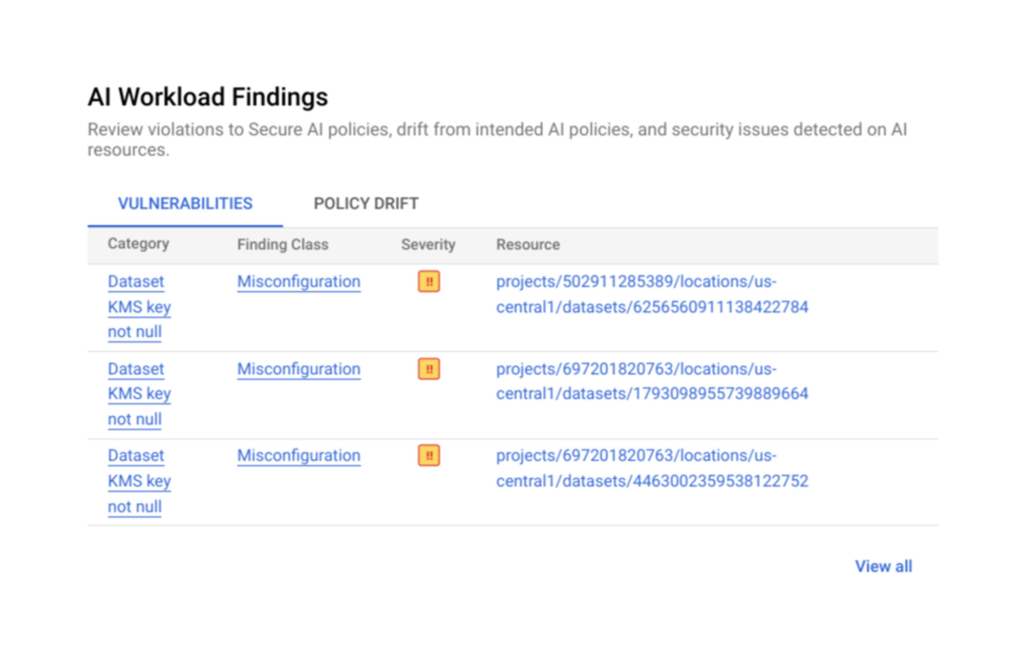
Reacting to security situations involving Vertex AI
Built-in risk analysis tools may be utilized to evaluate the problem and suggest next steps for remediation when Security Command Center identifies a Vertex AI workload operating outside of defined security boundaries. Among them is attack route simulation, which simulates the access and compromise of Vertex AI workloads by an actual attacker.
Security professionals are able to envision how a hacker would use certain holes in cloud security to get access to valuable resources. Additionally, it offers a score on attack exposure to aid in prioritizing cleanup.
Furthermore, information demonstrating the security posture of Vertex AI workloads is provided by Security Command Center. To ensure that the appropriate application or devsec team receives them, reports may be tailored for certain folders, projects, or assets.
Positioning controls to meet common criteria of compliance
Security Command Center offers pre-made policy sets for compliance requirements that may be used with different kinds of cloud apps, in addition to safeguarding AI workloads. Detective controls uphold accepted norms like:
- CIS 2.0
- CIS Kubernetes Benchmark v1.5.1
- NIST SP 800-53
- ISO 27001
- PCI DSS
FAQS
What is the security Command Center?
You get consolidated insight into Google Cloud resources using Security Command Center (SCC). SCC offers a single dashboard to assist you in preventing, identifying, looking into, and dealing with issues inside your company.
What are the benefits of security Command Center?
With the evaluation of your security and data attack surface, asset inventory and discovery, identification of misconfigurations, vulnerabilities, and threats, and assistance in mitigating and correcting risks, Security Command Center helps you fortify your security posture.
What is the purpose of a command center?
A command center, also referred to as a headquarters or HQ, is a central location for executing directives and overseeing activities. Three main activities are shared by all command centers: inputs, processes, and outputs.
How do I activate SCC premium?
An organization must choose between subscription-based pricing and usage-based pricing in order to activate the Premium tier. You may choose how much to charge for your Security Command Center depending on how much you use thanks to usage-based pricing.
How to setup security command center in gcp?
Navigate to the Security Command Center page in the Google Cloud interface. Choose the project, folder, or organization that needs service management. Select Settings from the menu. Click Manage settings for the service that you wish to change.
