Intel Trust Authority Use Cases
The biggest difficulty in data centers and clouds is AI. Compatible with different workloads, standalone, and hybrid cloud/edge deployment. Many AI activities require GPU acceleration. AI is changing finance, manufacturing, advertising, and healthcare. Firms spend millions on AI models with custom weights. Knowledge of competition model parameters is clever. Secret data sets used to train these models can enhance competitiveness. Thus, data and model owners seek usage, rest, and transit protection.
Confidential Computing’s hardware-hardened, certified Trusted Execution Environment (TEE) protects sensitive data and code for authorized users and applications. This includes AI workload model parameters, weights, and training/inference data. Confidential Computing Consortium has details.
Testimony and Trust
Confidential Computing requires attestation for stakeholder cryptographic confidence. The TEE’s configuration, security, and validity are validated. Launch and regular TEE runtime policy-based attestation are possible. Trusting the computer platform with sensitive data requires authentication.
CPU, GPU TEEs from Intel and NVIDIA Confidential Computing differ. To trust CPU and GPU TEEs, customers need two suppliers’ certification.
This Intel-NVIDIA alliance provides a uniform attestation solution for Confidential Computing CPU and GPU TEEs using Intel Xeon CPUs with Intel TDX and NVIDIA Tensor Core H100 GPUs. Xeons with Intel TDX extensions support hardware TEEs. Intel TDX isolates VMs from the VMM/hypervisor and other software outside the Trust Domain, preventing software attacks.
Intel CPU TEEs are verified in several methods. Customers, hosting Cloud Service Providers, or ISVs can establish private attestation services. CPU attestation will employ Intel Trust Authority, a new cloud-based independent trust solution. RAS verifies GPU-hosted TEEs.
1.Intel and NVIDIA revealed one attestation architecture at the secret computing summit.
2.Intel Trust Authority Client verifies CPU and GPU TEE attestation with SAAS.
3.NVIDIA driver, NRAS SaaS, or direct call GPU evidence acquisition is supported by the Client (Option 2).
4.All attestation evidence was confirmed in one call.
5.Attesting secret computing requires minimal app changes.
The picture shows Confidential Computing users two CPU and GPU attesting options. Call the Intel Trust Authority Client for full platform attestation and receive one token or CPU and GPU attestation and two tokens. Both Intel Trust Authority SaaS and NVIDIA NRAS verify CPU and GPU attestation.
Independent CPU TEE trust service
Client-based SaaS Intel Trust Authority verifies trustworthiness. Intel Trust Authority supports remote attestation with Intel CPU-based TEEs (SGX and TDX) and will support GPU-based and other hidden computing devices when available. Intel Trust Authority verifies public, private, and edge cloud trustworthiness. IETF-RATS verifies passports and backgrounds for Intel Trust Authority. Intel Trust Authority’s broad policy structure allows customer-defined CPU and GPU TEE assessment policies.
Remote TEE attestation using GPUs
GPU attestation reports are verified by SaaS-based NVIDIA Remote Attestation Service (NRAS). NRAS capabilities:
We accept GPU attestor proof.
Phone RIM Bundles (Golden Measurements) provide evidence comparison.
Check evidence and RIM signatures with NVIDIA OCSP.
Use RIM bundle certificate chain to verify.
Return EAT
The signed EAT is created by NRAS using a JSON Web Token. User or Relying Party can use NVIDIA Attestation SDK or NRAS APIs.
This article describes how this unified attestation works with Intel TDX TEEs on the CPU and NVIDIA H100-based TEEs on the GPU, as well as their workflows with Intel Trust Authority SaaS and NVIDIA NRAS. This approach simplifies and encapsulates application attestation. Applications call Intel Trust Authority Client APIs like collectCPUToken(), collectGPUToken(), and collectCompositeToken() to start attestation flows. These APIs handle the complexity of getting the TEE evidence as a signed report from the TEE hardware, transmitting it to the attestation services, and retrieving the signed attestation tokens. A signed EAT token with Intel Trust Authority CPU and GPU attestation tokens is returned by CollectCompositeToken().
Client Intel Trust Authority
The Intel Trust Authority Client must abstract the workflow to gather attestation evidence from TEEs and securely submit it to the Intel Trust Authority SaaS before beginning workloads in any TEE. Confidential Computing needs expandable Trust Authority Client. Intel Trust Authority Client requests CPU and GPU attestation, signed tokens, and certificates from Intel Trust Authority SaaS and NVIDIA NRAS.
We provide two strategies to connect Intel Trust Authority Client and SaaS to NVIDIA NRAS for H100 GPU attestation.
Option 1: Intel Trust Authority Client → SaaS → NRAS
See Option 1’s higher-level flow below.
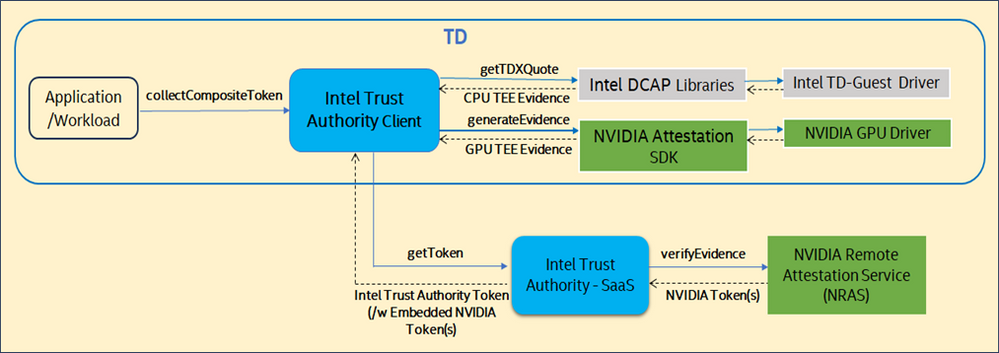
After obtaining attestation evidence from Intel TDX and H100 GPU, the Intel Trust Authority Client connects the Intel Trust Authority SaaS, which calls NRAS for the NVIDIA signed token with demonstrated proof.
1.Application uses Intel Trust Authority Client collectCompositeToken.
2.Intel Trust Authority SaaS nonce to client.
3.The Intel Trust Authority Client uses the NVIDIA Attestation SDK and nonce to retrieve the GPU driver’s CPU TEE (Intel TDX CVM) attestation report.
4.GPU drivers verify Intel Trust Authority Client.
5.The Client need SaaS’s signed EAT token GPU attestation policy and documentation. Application owners can set SaaS GPU attestation policy.
6.Intel Trust Authority SaaS verifies evidence with NRAS and collects the NVIDIA-signed token using the SDK.
7.Intel Trust Authority SaaS verifies the Client and issues a composite Intel Trust Authority signed Token with NVIDIA token(s).
8.Relying Party validates signed token and Intel Trust Authority SaaS token signing certificate.
Option 2: (Intel Trust Authority Client → NRAS)
See Option 2’s higher-level flow below.
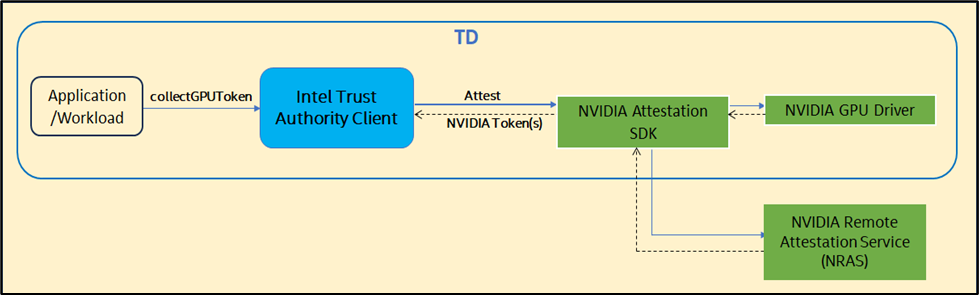
Instead of GPU TEE, the Intel Trust Authority Client calls NRAS for GPU attestation. NRAS remotely attests H100 GPU TEEs without Intel Trust Authority SaaS.
1.Use Intel Trust Authority Client collectGPUToken().
2.SaaS-signed nonce for Intel Trust Authority Client.
3.Intel Trust Authority Client obtains GPU driver attestation report in CPU TEE (Intel TDX CVM) using NVIDIA Attestation SDK with nonce.
4.GPU drivers verify Intel Trust Authority Client.
5.The Intel Trust Authority Client uses the NVIDIA SDK to verify and receive the signed token.
6.For verification, NRAS delivers the Intel Trust Authority Client the token signing certificate.
One API call checks environmental safety in Option 1, making it simpler. Option 2 is for those who wish to control each stage and enjoy its complexity.
Examine confidential training
To infer, models must be constructed and trained on masses of data. Storage, processing, and memory are typical for model training. This works well in the cloud but needs rest, transit, and use security. Figure displays concealed training reference architecture.
.Intel TDX CPU, NVIDIA H100 GPU TEEs. Key brokers and distribution services must process CPU and GPU attestation information before issuing TEE keys.
.After Intel Trust Authority verifies the Intel TDX CPU and H100 GPU, key broker services will send the model and data decryption keys to the Trust Domain.
.Without key broker decryption keys, the application will stop.


