Cloud SQL Auth Proxy
In this blog they will explain how to utilise the Cloud SQL Auth Proxy to create safe, encrypted data, and authorised connections to your instances. To connect to Cloud SQL from the App Engine standard environment or App Engine flexible environment, you do not need to configure SSL or use the Cloud SQL Auth Proxy.
The Cloud SQL Auth Proxy’s advantages
Without requiring authorised networks or SSL configuration, the Cloud SQL Auth Proxy is a Cloud SQL connection that offers secure access to your instances.
The following are some advantages of the Cloud SQL Auth Proxy and other Cloud SQL Connectors:
Secure connections:
TLS 1.3 with a 256-bit AES cypher is automatically used by this to encrypt traffic to and from the database. You won’t need to administer SSL certificates because they are used to validate the identities of clients and servers and are not dependent on database protocols.
Simpler authorization of connections:
IAM permissions are used by the Cloud SQL Auth Proxy to restrict who and what can connect to your Cloud SQL instances. Therefore, there is no need to supply static IP addresses because it manages authentication with Cloud SQL.
It depends on the IP connectivity that already exists; it does not offer a new way for connecting. The Cloud SQL Auth Proxy needs to be on a resource that has access to the same VPC network as the Cloud SQL instance in order to connect to it via private IP.
The operation of the Cloud SQL Auth Proxy
A local client that is operating in the local environment is required for the Cloud SQL Auth Proxy to function. Your application uses the common database protocol that your database uses to connect with the Cloud SQL Auth Proxy.
It communicates with its server-side partner process through a secure channel. One connection to the Cloud SQL instance is made for each connection made via the Cloud SQL Auth Proxy.
An application that connects to Cloud SQL Auth Proxy first determines if it can establish a connection to the target Cloud SQL instance. In the event that a connection is not established, it makes use of the Cloud SQL Admin APIs to acquire an ephemeral SSL certificate and connects to Cloud SQL using it. The expiration date of ephemeral SSL certificates is around one hour. These certificates are refreshed by Cloud SQL Auth Proxy prior to their expiration.
The only port on which the Cloud SQL Auth Proxy establishes outgoing or egress connections to your Cloud SQL instance is 3307. All egress TCP connections on port 443 must be permitted since Cloud SQL Auth Proxy uses the domain name sqladmin.googleapis.com to use APIs, which does not have a stable IP address. Make that your client computer’s outbound firewall policy permits outgoing connections to port 3307 on the IP address of your Cloud SQL instance.
Although it doesn’t offer connection pooling, it can be used in conjunction with other connection pools to boost productivity.
The connection between Cloud SQL Auth Proxy and Cloud SQL is depicted in the following diagram:
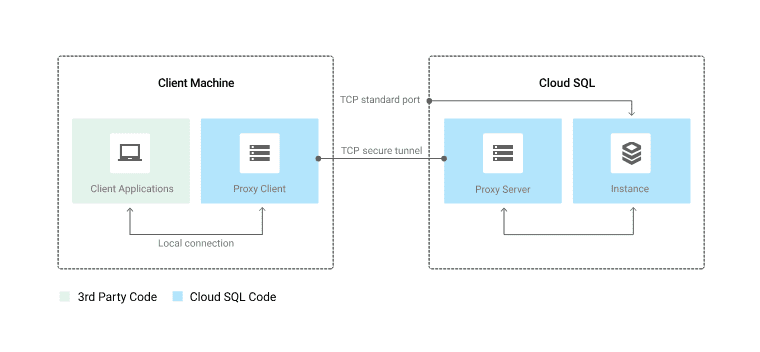
Use of the Cloud SQL Auth Proxy Requirements
The following conditions must be fulfilled in order for you to use the Cloud SQL Auth Proxy:
- Enabling the Cloud SQL Admin API is necessary.
- It is necessary to supply Google Cloud authentication credentials to this.
- You need to supply a working database user account and password to this proxy.
- The instance needs to be set up to use private IP or have a public IPv4 address.
It is not necessary for the public IP address to be added as an approved network address, nor does it need to be reachable from any external address.
Options for starting Cloud SQL Auth Proxy
You give the following details when you launch it:
- Which Cloud SQL instances to connect to so that it can wait to receive data from your application that is sent to Cloud SQL
- Where can it locate the login credentials needed to validate your application with Cloud SQL?
- Which type of IP address to use, if necessary.
- Whether it will listen on a TCP port or a Unix socket depends on the startup parameters you supply. It creates the socket at the specified location, which is often the /cloudsql/ directory, if it is listening on a Unix socket. The Cloud SQL Auth Proxy by default listens on localhost for TCP.
For authentication, use a service account
To authorise your connections to a Cloud SQL instance, you must authenticate as a Cloud SQL IAM identity using this Proxy.
For this purpose, the benefit of using a service account is that you may make a credential file particularly for the Cloud SQL Auth Proxy, and as long as it approach for production instances that aren’t operating on a Compute Engine instance is to use a service account
In the event that you require this to be invoked from several computers, you can replicate the credential file within a system image.
You have to make and maintain the credential file in order to use this method. The service account can only be created by users who possess the resourcemanager.projects.setIamPolicy permission, which includes project owners. You will need to get someone else to create the service account or find another way to authenticate this, if your Google Cloud user does not have this permission.

