Contents [hide]
What are Cloud Containers?
Containers are software executable units that include the application code, libraries, and dependencies. They make it possible for code to operate in any type of computer environment, including desktop, cloud, and conventional IT.
Containers utilize a type of operating system (OS) virtualization whereby the OS kernel’s features such as Linux namespaces and cgroups, Windows silos, and task objects can be used to isolate processes and manage how much CPU, memory, and disc space they have access to.
Modern cloud-native apps now use containers as their de facto compute units because they are more portable and resource-efficient than virtual machines (VMs). Furthermore, containers are essential to the underlying IT architecture that supports hybrid multicloud environments, which include on-premises, private, public, and multiple cloud services from multiple cloud providers.
The global container technology market is projected to increase at a compound annual growth rate (CAGR) of 19.8% from its 2021 valuation of USD 496.4 million to USD 3123.42 million by 2031, according to a report from Business Research Insights.
Cloud Containers definition
Containers are small packages that include your application’s code together with dependencies, including particular runtime versions for programming languages and libraries needed to operate your software.
Cloud containers management
A cloud container is just a container that operates on cloud infrastructure instead of a data center or a local computer. In cloud computing, containers are image files that have all of the necessary components for software to function, including libraries, runtime, code, environment variables, and configuration files.
The images are built in layers, with a base image (often a stripped-down version of an operating system) as the starting point. Additional layers are added in accordance with instructions found in a container configuration file. The immutability of container images the fact that they remain unchanged after creation is one of their primary characteristics. It is possible to save photos in a container registry and use them consistently in various cloud settings.
Here is a summary of the various facets of container technology.
Container Runtime
Container runtimes are in charge of actually executing containers. They oversee the lifecycle, execution, and resource segregation of containers. Within the user area of the cloud instance operating system, containers function as separate processes. Despite sharing the host operating system, they are kept apart from the host and one another. Effective resource allocation is made possible by this separation, where the runtime sets restrictions to prevent resource contention between containers.
Establishing connections
Cloud containers can be set up with their own separated network stacks, which prevents applications running in different containers from interfering with one another. Predefined network channels and port mapping control communication between containers and with the outside world.
Keep in storage
Ephemeral storage is commonly used in cloud containers, which means that any information written to the writable layer of the container is erased when the container shuts down. Cloud storage volumes can be used for long-term storage. The lifecycle of the container has no bearing on these quantities, which can be shared by other containers.
Arrangement
Orchestration technologies facilitate multiple container deployment, scaling, and management in large-scale applications. In order to manage failover procedures and balance the load, the tools disperse these containers among a group of cloud servers. Containerized application maintenance in complex contexts is made much easier by automation. Without having to execute operations on each and every cloud instance, you can create and manage sophisticated, large-scale containerized apps across hybrid cloud infrastructures. Instead of sending a container image file to every instance by hand, you can configure the orchestration tools to automatically deploy the image files to cloud instances by pulling them from the container registry.
Benefits of Containers in Cloud
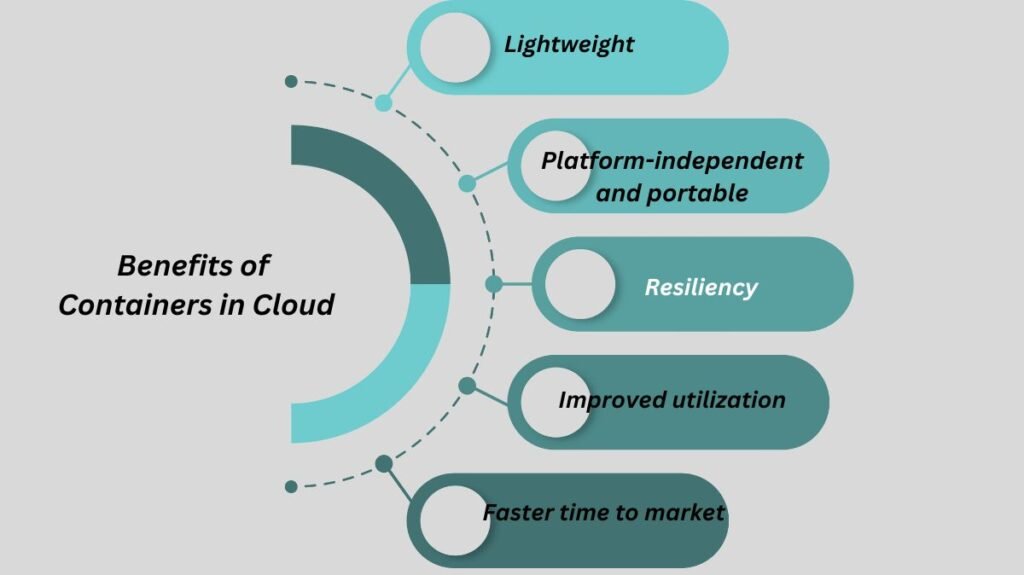
The main benefit of containers is that they offer a degree of abstraction that makes them portable and lightweight, particularly when compared to virtual machines (VMs). Their main advantages are as follows:
Lightweight
Because containers share the machine’s operating system kernel, each program does not require a separate OS instance, thus container files are tiny and resource-efficient. Because containers are smaller, they can boot up faster and support cloud-native apps that scale horizontally better than virtual machines (VMs).
Platform-independent and portable
Because containers bring all of their dependencies with them, software may be built once and operate across computing environments (such laptops, the cloud, and on-premises) without requiring configuration changes.
Supportive of contemporary architecture and progress
Containers’ small size, deployment portability, and platform consistency make them perfect for contemporary development and application paradigms like DevOps, serverless, and microservices, which are constructed by frequent code deployments in tiny increments.
Enhanced utilization
Similar to virtual machines (VMs), containers let developers and operators make better use of the CPU and memory on actual devices. Because containers facilitate microservices design, which allows for more granular deployment and scaling of application components, they go even farther. This is a compelling substitute for expanding a monolithic application since only one component is having trouble handling its load.
Quicker time to market
Because containers use fewer system resources than virtual machines (VMs), they may be managed and deployed more quickly. This functionality maximizes time to market while saving money and effort on application deployment.
Container use cases
Companies utilize containers to facilitate the following:
Micro-services
Because containers are lightweight and compact, they work well with microservice designs, which build applications from numerous smaller services that can be independently deployed and are loosely connected.
DevOps
A common foundation for many development and operations teams that use DevOps approaches is the combination of containers as a platform and microservices as an architecture. Containers, for example, facilitate DevOps pipelines, which include the establishment of continuous integration and continuous deployment (CI/CD).
Both hybrid and multicloud
In hybrid cloud and multicloud scenarios, where organizations operate across a mix of several public clouds in addition to their own data center, containers are a great underlying architecture since they can function reliably across laptops, on-premises, and cloud environments.
Modernization and migration of applications
Preparing apps for cloud migration through containerization is one of the most popular methods for modernizing programs.
ML and AI workloads
Artificial intelligence (AI) and machine learning (ML) applications can be swiftly deployed into cloud computing environments by DevOps pipelines using containerization, which is the orchestration of Docker images with Kubernetes.
Generative AI
When combined with orchestration tools, containers provide a scalable and portable solution for managing and deploying the large language models (LLMs) linked to generative AI. Additionally, it is possible to rapidly package modifications to the LLM into a fresh container image, which speeds up testing and development.
Cloud Container security
Because containers are essential to software development and deployment in hybrid cloud environments, businesses must make sure that their containerized workloads are protected from both internal and external security risks.
The deployment of containers in any location opens up new attack vectors for the container-based environment. Host operating systems, container runtimes, container orchestration platforms, image registries, and container images are among the security flaws.
First and foremost, businesses must incorporate container security into their overall strategy and security policy. Along with cloud-based security software tools, these initiatives must incorporate security best practices. Throughout the whole container lifespan, containerized apps and the infrastructure supporting them should be safeguarded by this all-encompassing strategy.
Assuming that the security of a complex network is constantly vulnerable to both internal and external threats, a zero-trust approach is one of the best security approaches. Containers also require a DevSecOps methodology. The application development methodology known as DevSecOps automates the incorporation of security principles at each stage of the software development lifecycle, including design, integration, testing, delivery, and deployment.
Additionally, in order to reduce risks, organizations must use the appropriate container security solutions. Configuration management, network segmentation, access control, malware or cyberattack detection, monitoring, and more are examples of automated security systems.
To make sure that containerized workloads comply with legal and regulatory requirements such as GDPR, HIPAA, etc., software tools are also available.

