Cloud Computing Planning Phases
You must think about your company needs before deploying apps to the cloud. Observing are the things that one has to consider:
- The need for data security and privacy
- Financial Needs
- Cloud type: hybrid, private, or public
- The need for data backup
- Requirements for training
- Requirements for dashboards and reporting
- Requirements for client access
- Requirements for data export
How many phases are present in cloud computing planning
A thorough planning process is required to fulfill all of these needs. The following figure provides descriptions of each of these planning stages:
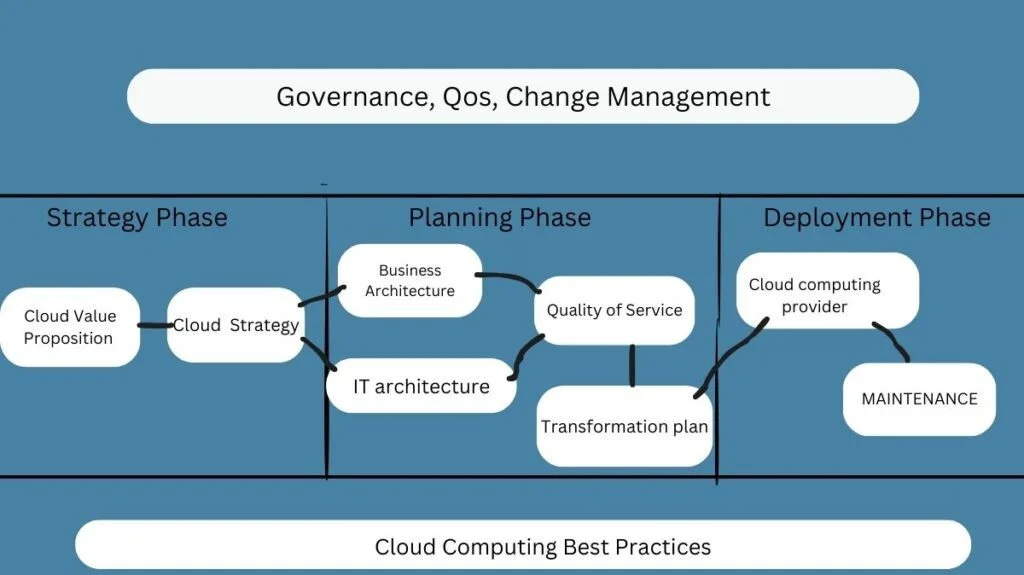
Strategy Planning Phase
Here, we examine the potential strategic issues that customers may encounter. This analysis may be completed in two steps:
- The Value Proposition of Cloud Computing
- Planning a Cloud Computing Strategy
Cloud Computing value proposition
Here, we examine the variables that affect clients’ decisions to use cloud computing and focus on the main issues they want resolved. These crucial elements are:
- Simplifying IT management
- A decrease in the cost of operation and maintenance
- Innovation in business modes
- Inexpensive hosting for outsourcing
- Excellent outsourcing hosting service quality.
All of the aforementioned analysis aids in making decisions for further developments.
Cloud Computing strategy Planning
The analytical outcome of the previous stage serves as the foundation for the strategy’s development. This stage involves creating a strategy paper based on the potential challenges a client may have when utilizing cloud computing mode.
Cloud Computing Tactics Planning Phase
This stage analyzes the risks and issues with the cloud application to make sure that the clients’ business objectives are effectively met by cloud computing. The following planning steps are included in this phase:
- Development of Business Architecture
- Development of IT architecture
- Quality of Service Development Requirements
- The creation of a transformation plan
Development of Business Architecture
In this stage, its identify the potential business risks associated with cloud computing applications.
Development of IT architecture
This stage involves determining the technology needed to enable corporate apps and data systems as well as the applications that support business operations.
Quality of Service Development Requirements
Quality of service includes reliability, security, disaster recovery, and other non-functional factors. These non-functional elements are necessary for the cloud computing mode to be implemented successfully.
The creation of a transformation plan
In this stage, it create all the plans needed to switch the company’s present operations to cloud computing.
Phase of Cloud Computing Deployment
Both of the aforementioned phases are the emphasis of this phase. The two steps involved are as follows:
- Cloud computing provider
- Maintenance and Technical Service
Cloud computing provider
This step selects a cloud provider based on its Service Level Agreement (SLA), which establishes service quality.
Maintenance and Technical Service
The cloud provider offers technical and maintenance services. They must be required to guarantee the caliber of services.
Cloud Computing Architecture
The architecture of cloud computing is made up of numerous loosely linked cloud components. The cloud architecture can be roughly separated into two sections:
- Front End
- Back End
Cloud computing architecture diagram
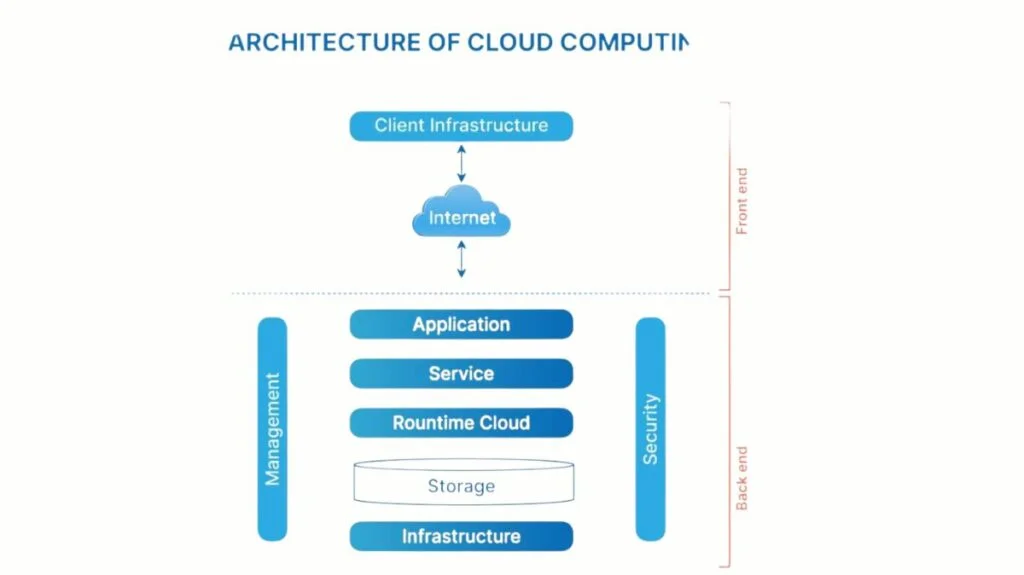
Front End
The client portion of a cloud computing system is referred to as the front end. It includes programs and interfaces, including web browsers, that are necessary to access cloud computing services.
Back End
The term “back end” describes the actual cloud. It includes every resource needed to deliver cloud computing services. It includes servers, virtual machines, security measures, services, deployment strategies, and large data storage, among other things.
Key Points
- The back end is in charge of providing protocols, traffic control, and built-in security measures.
- The server uses middleware, which is a set of protocols, to facilitate communication between the linked devices.


[…] is a cloud computing architecture that uses the internet to deliver resources including storage, network, and processing power. It […]
[…] each with its own operating system and applications, on a single physical machine. It also powers cloud computing services that help enterprises manage […]
[…] most crucial aspect of cloud computing is server virtualization. Thus, cloud computing is a combination of the phrases cloud and […]