Google Cloud Security Command Center
The ways in which virtual red team technologies might identify critical security flaws before intruders do. Cloud-native application protection platforms (CNAPPs) are a useful tool used by cloud security teams to identify vulnerabilities and misconfigurations in multi-cloud settings. Where am I most at risk? is one of the two basic cloud security concerns that many of these solutions miss, despite the fact that they may find thousands of possible security vulnerabilities in huge cloud settings. and “Which matters should I give priority to?”
With its virtual red team capacity, Cloud Security Command Center can assist in providing answers to both queries. A crafty and determined attacker is simulated by the virtual red team. It finds vulnerabilities in cloud defenses that an external attacker may exploit by running millions of attack permutations against a digital twin model of an organization’s cloud environment.
Crucially, the virtual red team can identify attack pathways with toxic combinations specific to the cloud environment of each client. Groups of security flaws known as “toxic combinations” have the potential to open up a route for an attacker to get valuable cloud resources. These resources might be virtual machines (VMs) running mission-critical applications or databases containing sensitive client data.
Unlike the static, rules-based approach used by most CNAPPs, this simulation-based method of revealing cloud concerns is unique. Customers of Cloud Security Command Center may use it to identify previously unseen attack vectors with toxic combinations, enabling them to respond to cloud threats more successfully.
Toxic Combinations
The significance of toxic combinations
Thousands of resources may be found in cloud environments, and some of them can have security or compliance problems due to misconfigurations, software vulnerabilities that might be exploited, or just plain violations of company policies. But not every one of these problems carries the same amount of danger.
A virtual machines (VMs) in a development environment that is separated from the production environment is not the same as a VM configured with a public IP address that may access a storage bucket that has customer data and has a known vulnerability. The latter has to be addressed right now, while the former can wait.
Cloud security teams may identify and rank these important concerns with the aid of Cloud Security Command Center.
Early methods for identifying toxic combinations
Many CNAPP solutions revolve on the finding of toxic combinations. Writing and implementing rules is the standard method for identifying items that clearly pose a danger. Although this may have instant benefits, there are a few issues that quickly surface:
- First, what constitutes a toxic combination or high-risk attack path? To identify cloud security vulnerabilities, most suppliers use static rules. This means that in order to identify hazards in even somewhat sophisticated cloud settings, people must develop a great deal of rules and continuously update them in order to stay up with emerging threats.
- A rule-based strategy has inherent limitations. It is limited to identifying known attack pathways with toxic combinations. Is there anybody aware of every potential danger that exists in a cloud environment? Could they create guidelines for each one of them if they did?
- Because cloud systems may be quite dynamic, it’s important to execute rules regularly in order to identify emerging threats. The findings might easily become outdated if they are not conducted often.
The operation of virtual red teaming
Using virtual red teaming technology which mimics a determined and experienced attacker trying to get past your cloud protections and compromise your valuable assets Cloud Security Command Center discovers toxic combinations.
It use a simulation engine that tests a digital twin replica of your cloud environment with millions of attack variants. It searches for every route an attacker may take to get access to private cloud resources. Once it has located them, it indicates potential attack locations for outside parties and pinpoints cloud services that may be vulnerable. Security teams may reduce cloud risks before attackers take advantage of them by prioritizing their reactions to attacks with the aid of virtual red teaming.
It may identify threats that either have no documented rules or have not been considered by the rule development team of a security provider. By letting go of static criteria, SCC can identify hazards specific to each cloud environment and reduces the likelihood of overlooking important exposure spots.
Virtual red teaming
The following are some actual threats that it have identified using virtual red teaming in cloud environments:
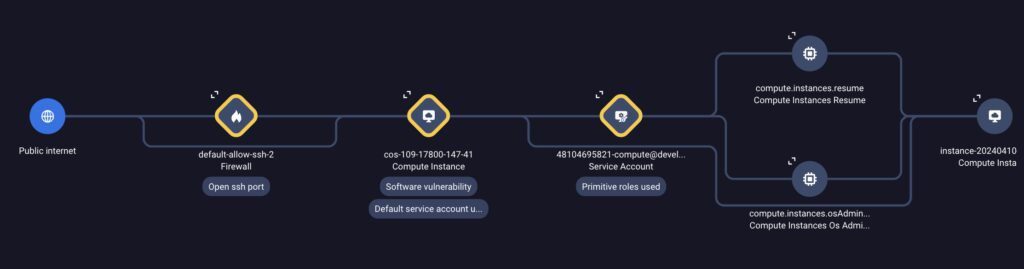
- An attacker may locate and establish a connection with a publicly available virtual machine (VM) for a retail client, after which they might take advantage of a commonly exploited vulnerability to get elevated privileges. With these rights, it would be possible to log into a second virtual machine (VM) that was running a crucial business application and then restore activities on the halted VM.
- SCC discovered that an attacker may take control of a compute instance in a cloud environment for a financial services client, then exploit privileges in an over-privileged service account to migrate laterally to another compute instance. The attacker might then utilize the administrator credentials and other permissions granted to the instance service account on that second instance. With these administrator rights, the attacker may create an that permits read, write, and delete access to a private bigquery dataset.
- SCC discovered that an attacker might phish a user and get access to a related cloud service account for a client in the healthcare sector. The attacker might then get access to many high-value resources by creating new keys for additional service accounts using the privileges of this service account.
These more intricate situations highlight the kinds of cloud hazards that are difficult for strictly rule-based methods to identify. With the ability to reveal problems you may not have realized existed, Cloud Security Command Center offers a more effective method of assisting you in identifying the biggest threats in your multicloud system. It assist security managers in becoming knowledgeable about cloud risk so they can safeguard their critical data and apps in the cloud.


