Understanding Difference Between Containers And Hypervisor
Contents
Type 1 Hypervisor Vs Type 2
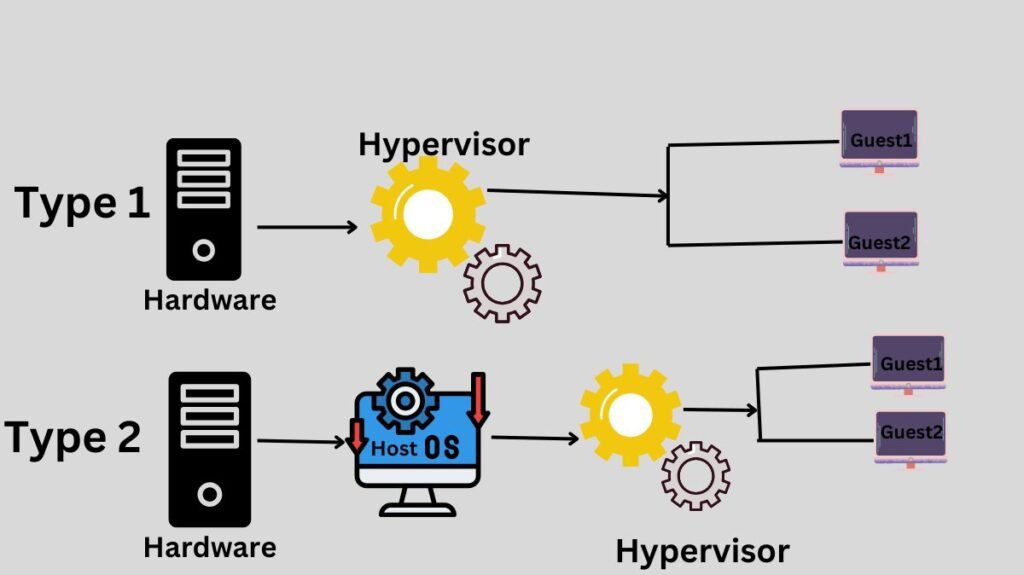
As indicated, it separate virtual machines (VMs) from the hardware below, ensuring each gets the resources it needs.
The procedure begins with the host computer running a it and installing it as an application. From there, it communicates with the operating system of the host computer. After that, it creates separate virtual environments on the host computers by loading the virtual machines’ client operating systems.
By assigning resources like memory, bandwidth, and storage for each virtual machine (VM),it serves as a bridge between the VMs and the actual hardware. The execution of resources is still managed by the actual hardware. For instance, although the it controls the schedule, the central processing unit (CPU) continues to carry out CPU commands as required by the virtual machines.
API calls are the main way virtual machines (VMs) and real computers interact with it.
Hypervisor Types
The main hypervisors are type 1 and type 2.
Type 1 Hypervisor
A type 1 hypervisor operates directly on the hardware of the underlying computer, interfacing with its memory, physical storage, and central processor unit (CPU). Because of this, type 1 hypervisors are sometimes known as native or bare-metal it. A type 1 hypervisor replaces the host OS.
Due to their direct access to real hardware, Type 1 hypervisors are incredibly efficient. Because there is nothing between them and the CPU that an attacker may compromise, this capability also makes them more secure. However, in order to manage several virtual machines and manage the host hardware, a type 1 hypervisor frequently needs a separate management computer.
Type 2 Hypervisor
Often called an embedded or hosted hypervisor, a type 2 hypervisor does not operate directly on the underlying hardware. Rather, it functions as an OS application. Seldom do Type 2 hypervisors appear in server-based settings. Instead, they work well for users of individual PCs who need to run several operating systems. Engineers, security experts who examine viruses, and business customers that want access to apps that are only available on other software platforms are a few examples.
Type 2 hypervisors frequently come with extra toolkits that users may install on the guest operating system. These technologies offer improved connectivity between the host and guest operating systems, typically allowing the user to view host OS files and directories from within the guest virtual machine or to cut and paste between the two.
In addition to the primary guest operating system running on the host system, a type 2 hypervisor facilitates rapid and simple access to a backup guest OS. This feature boosts end-user productivity. For instance, a user may utilize it to access their preferred Linux-based programming tools while utilizing a vocal dictation system that is exclusive to Windows.
However, a type 2 hypervisor creates latency problems that might impact performance since it has to access memory, computational, and network resources through the host operating system. Because an attacker might control any guest operating system running in the type 2 hypervisor, it also presents possible security problems in the event that the host operating system is compromised.
Reference Models for Hypervisors
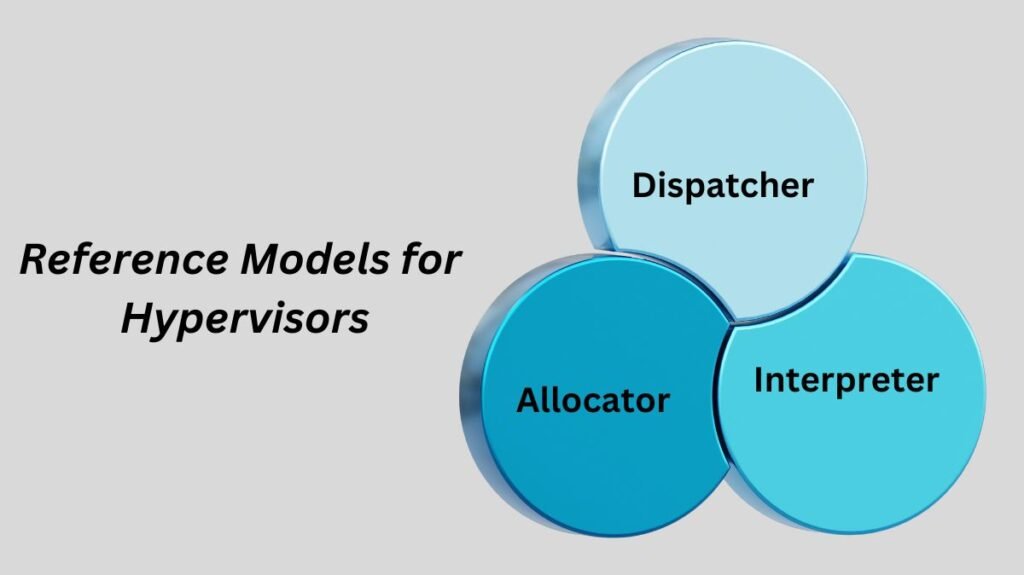
Three main module coordinates imitate hardware:
Dispatcher
The dispatcher redirects the virtual machine instance’s commands to one of the other two modules, acting as the monitor’s entry point.
Allocator
The decision of which system resources to give the virtual machine instance rests on the allocator. This implies that the dispatcher calls the allocator each time a virtual machine attempts to carry out an instruction that modifies the machine resources linked to the virtual machine.
Interpreter
Interpreter procedures make up the interpreter module. Every time a virtual machine carries out a privileged instruction, they are carried out.
What Security Factors Apply To Hypervisors?
There is a certain level of security since software on a virtual machine doesn’t interfere with applications on other guest operating systems. But for a strong security posture, the virtualized environment depends on it. All virtual machines running on top it will be impacted by any problems that affect it. Therefore, to ensure the integrity of the workload, it is imperative to employ a it with built-in security features.
Difference Between Hypervisor And Container
| Aspect | Hypervisors | Containers |
|---|---|---|
| Definition | A software layer that abstracts hardware, allowing multiple operating systems to run on one host. | A software package containing all files and configurations needed to run an application. |
| Virtualization Level | Operates at the hardware level, virtualizing physical hardware resources. | Operates at the operating system level, virtualizing the OS for multiple applications. |
| Resource Usage | Typically uses more resources as it runs multiple operating systems. | More lightweight, as it shares the same operating system kernel across all containers. |
| Isolation | Provides strong isolation between virtual machines (VMs), including separate OS instances. | Offers process-level isolation but shares the OS kernel, leading to less strict isolation. |
| Startup Time | Slower startup time due to loading entire operating systems for each VM. | Faster startup time as only the application and its dependencies need to be loaded. |
| Performance Overhead | Higher, as it involves running multiple OS instances. | Lower, as it avoids the overhead of running separate operating systems. |
| Use Cases | Ideal for scenarios requiring different operating systems or highly secure environments. | Best suited for application deployment, microservices, and environments with consistent OS needs. |
| Examples | VMware, Hyper-V, KVM | Docker, Kubernetes, Podman |