AWS GuardDuty EC2
Amazon GuardDuty is an intelligent threat detection and security monitoring service that leverages machine learning (ML) to analyse and process a variety of AWS data sources. It also continuously scans your workloads and AWS accounts for malicious activity and provides comprehensive security findings for visibility and remediation.
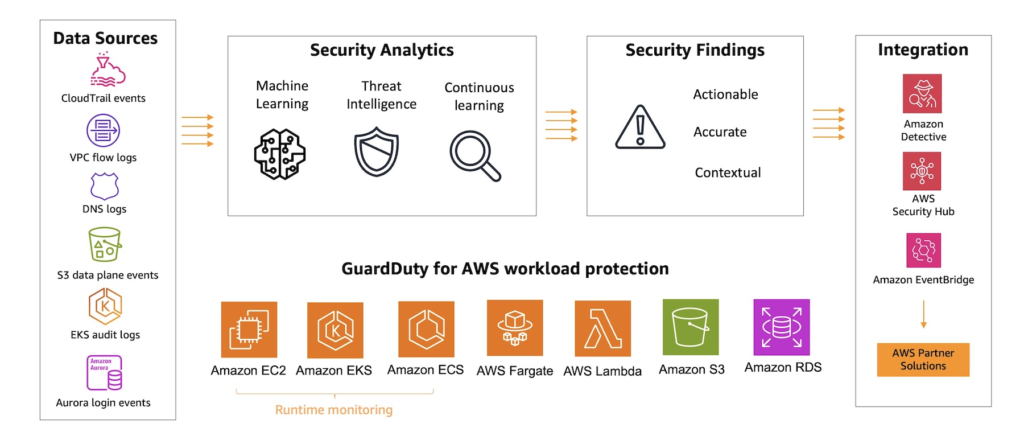
He adores the GuardDuty Runtime Monitoring tool, which examines file, network, and operating system (OS)-level events to identify possible runtime risks for certain AWS workloads in your environment. In March 2023, he initially announced that this capability will be available to all Amazon Elastic Kubernetes Service (Amazon EKS) resources. Seb reported about the preview for workloads on Amazon Elastic Compute Cloud (Amazon EC2) in November 2023, as well as the extension of the Runtime Monitoring functionality to include threat detection for AWS Fargate and Amazon Elastic Container Service (Amazon ECS).
AWS is pleased to announce today the general availability of Amazon GuardDuty EC2 Runtime Monitoring, which continuously monitors VPC Flow Logs, DNS query logs, and AWS CloudTrail management events to enhance threat detection coverage for EC2 instances at runtime and supplement the anomaly detection already offered by GuardDuty. You may now see actions at the OS and container levels as well as on-host information about risks that have been identified.
You can recognise and address any attacks that might target the computing resources in your EC2 workloads with GuardDuty EC2 Runtime Monitoring. Remote code execution that results in the download and execution of malware is a common threat to EC2 workloads. Those that are connecting to IP addresses linked to cryptocurrency-related activities or to IP addresses used by malware for command-and-control might be instances or self-managed containers in your AWS environment.
You may identify risks during the early breach and before they become events that have a significant effect on your organisation by using GuardDuty Runtime Monitoring, which gives you insight into suspicious actions that entail malicious file downloads and execution at every stage. AWS Organisations simplifies security by centrally enabling runtime threat detection for accounts and workloads.
AWS GuardDuty’s EC2 Runtime Monitoring
In the GuardDuty console, you may activate GuardDuty EC2 Runtime Monitoring with a few clicks. Runtime Monitoring must be enabled before using it for the first time.
For a duration of thirty days, any client who has never used the EC2 Runtime Monitoring function before may test it out for free and access all features and detection results. The number of days remaining in the free trial is shown on the GuardDuty interface.
At this point, you may configure the GuardDuty security agent for each specific EC2 instance that you want to keep an eye on in terms of runtime behaviour. The GuardDuty security agent may be installed manually or automatically. Enabling Automated agent setup at GA is an option that most clients choose since it lets GuardDuty handle the security agent on their behalf.
Using an Amazon Virtual Private Cloud (Amazon VPC) interface, the agent will be installed on EC2 instances using AWS Systems Manager and will collect runtime events related to your resource. See Managing the security agent Amazon EC2 instance manually in the AWS documentation if you want to manually administer the GuardDuty security agent. Delegated GuardDuty administrator accounts use AWS Organisations to administer their member accounts in multi-account scenarios.
The covered EC2 instances list, account ID, coverage status, and whether the agent is able to receive runtime events from the appropriate resource are all shown on the EC2 instance runtime coverage tab after you activate EC2 Runtime Monitoring.
You still have defence in depth for your EC2 instance even if the coverage state is Unhealthy, which indicates that it is not presently able to receive runtime discoveries. GuardDuty keeps an eye on AWS CloudTrail, VPC traffic, and DNS logs related to the EC2 instance in order to continue providing threat detection services.
View the results of the GuardDuty EC2 Runtime security audit
You may check the specifics of the healthy information when GuardDuty produces security findings and identifies a possible danger.
To see security findings unique to Amazon EC2 resources, choose Findings from the left pane. The results table may be filtered using the filter bar according to certain parameters, such the Resource type of Instance. Depending on the resource role that is, whether the EC2 resource was the actor conducting the activity or the target of suspicious behaviour the results’ specifics and degree of severity vary.
With today’s release, they enable more than thirty runtime security discoveries for EC2 instances, including the identification of backdoors, exploited domains, cryptocurrency-related activities, and unsanctioned communications.
Address the EC2 security issues you found
To learn more, choose each EC2 security finding. You may look up all the details related to the discovery and check to see whether the resource in issue is acting as you would anticipate.
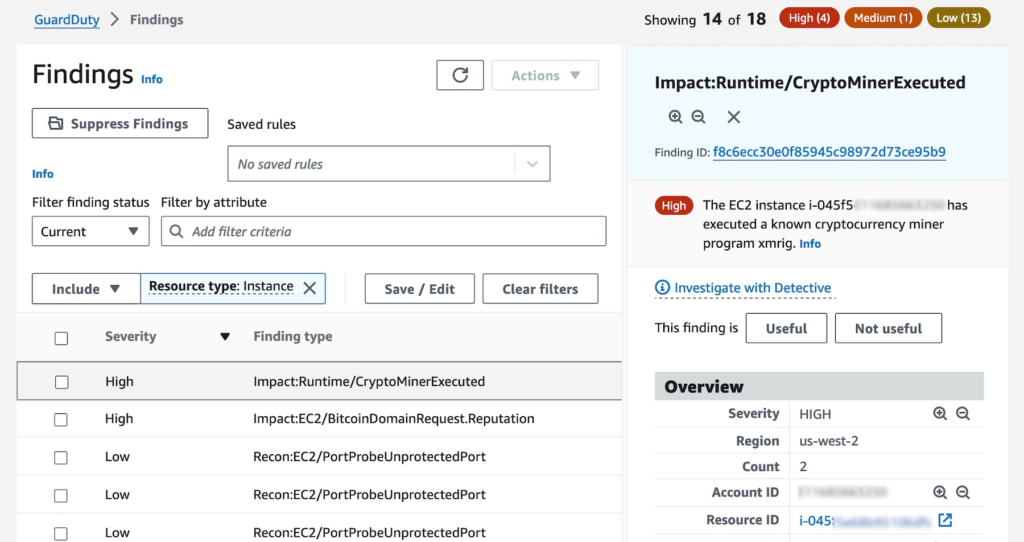
Suppression rules or trusted IP lists may be used to stop false positive alerts for that resource if the activity is allowed. The best course of action in terms of security is to presume that the instance has been hacked if the behaviour is unexpected and follow the steps outlined in the AWS documentation under Remediating a possibly compromised Amazon EC2 instance.
AWS Security Hub and Amazon Detective are two more AWS security services that can be integrated with GuardDuty EC2 Runtime Monitoring. Alternatively, you may utilise Amazon EventBridge, which enables you to initiate automatic and semi-automated actions, such isolating a workload for inspection, or leverage connectors with security event management or workflow systems, like Splunk, Jira, and ServiceNow.
You may quickly and simply examine security vulnerabilities by using Detective-created visualisations for AWS services when you choose examine with Detective.
Important information
Support for GuardDuty EC2 Runtime Monitoring for EC2 instances running Amazon Linux 2 or Amazon Linux 2023 is now available. It is possible to set the agent’s maximum CPU and memory restrictions.
Select use in the left pane to get an estimate of GuardDuty’s typical daily use charges. You may get an idea of how much things will cost you beyond the trial time during the 30-day free trial period. They charge you for the monitoring agents based on the number of vCPU hours recorded each month after the trial period ends.
You may save money on your GuardDuty costs by turning on EC2 Runtime Monitoring as well. You won’t be charged for GuardDuty fundamental protection VPC Flow Logs obtained from the EC2 instances hosting the security agent while the functionality is activated. This is because the security agent has comparable, but more contextualised, network data accessible. Furthermore, even in the event that an agent encounters outage, GuardDuty will continue to scan VPC Flow Logs and create pertinent discoveries, ensuring that you continue to get network-level security coverage.
Currently accessible
With the exception of AWS GovCloud (US) Regions and AWS China Regions, Amazon GuardDuty EC2 Runtime Monitoring is now accessible in all AWS Regions where GuardDuty is provided. Please see the complete list of regions where EC2 Runtime Monitoring is offered.
