Customers’ most frequent inquiries to Dell and Intel are about BIOS security. This shouldn’t come as a surprise because, in recent years, BIOS and other firmware have been recognized as expanding attack avenues. Additionally, Dell and Intel are working together to safeguard BIOS through a number of cutting-edge, “built-in” security mechanisms because we are committed to minimizing the attack surface in hardware.
Hardware and firmware protections that are incorporated into a device are referred to as BIOS security. This covers features like downgrade protection, resilience, and BIOS verification. These capabilities not only deter attacks but also respond to attacks by giving IT and security personnel the visibility and information they need to take appropriate action when suspicious activity is noticed inside the fleet.
BIOS Security in OptiPlex Series:
The BIOS is accessible to cybercriminals through a variety of entry methods. Direct physical access to the equipment can enable an assault, as can a straightforward email, which, according to the FBI Internet Crime Report for 2022, caused adjusted losses of nearly $2.7 billion in the United States. Additionally, without sufficient security measures, including ignorance of the state of the BIOS in your fleet, it is possible for your organization to overlook a breach. And not knowing something is a genuinely terrible state to be in.
How Dell Assists Users in Protecting the BIOS
Dell commercial machines arrive with SafeBIOS, a set of features that assist prevent BIOS assaults, identify potential compromise, and react by informing IT if anomalies are identified, to safeguard this crucial layer. Dell’s commercial PCs*, including the OptiPlex, Latitude, and Precision, provide post-boot BIOS verification, enabling IT to check the status of the BIOS across the fleet. SafeBIOS provides these features off-host rather than storing BIOS data on the hardware itself, which makes it vulnerable to corruption. This function, exclusive to Dell, compares a specific BIOS image against the “known good” copy using a secure cloud environment.
With Indicators of Attack, another Dell-only technology, SafeBIOS also automates the early detection of BIOS events and high-risk behaviors. Before the fleet becomes infected, we created the continuous extraction and analysis of changes in BIOS configurations and events to identify vulnerable endpoints for repair.
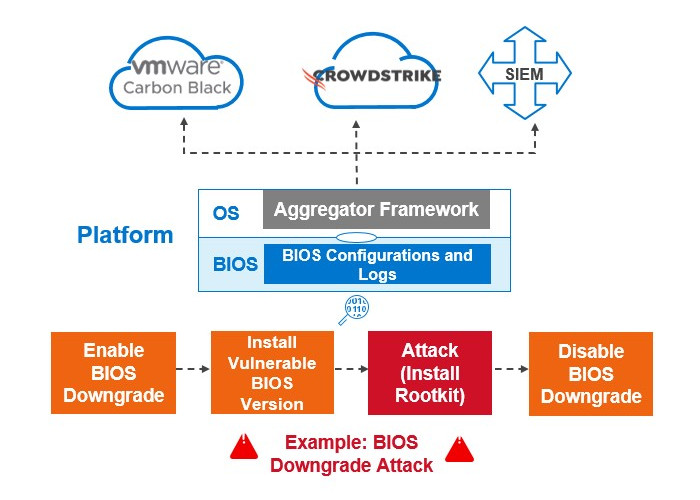
System hardware functioning “below” the operating system (OS), an area where IT managers previously had little to no control, is now visible and under control thanks to Dell SafeBIOS.
Bringing Intel to the Table
A comprehensive silicon-based solution for business PC security has been produced as a result of Dell and Intel’s focus on hardware-based security. These abilities consist of:
Intel Hardware Shield combined with Intel vPro. Each commercial Dell device running on the Intel vPro platform comes with Intel Hardware Shield, which offers fundamental hardware protection with cutting-edge security technologies that help safeguard all tiers in the computing stack. Dell makes use of these tools to offer its clients the most secure commercial PCs available on the market.
Intel BIOS Security. By strengthening the agent that may update the flash, Intel BIOS Guard lowers the possibility of BIOS attacks supported by flash. It makes the platform more safe by removing software surfaces and attackable surfaces that may write and wipe the flash, ensuring resilience.
iBoot Guard by Intel. The purpose of Intel Boot Guard is to safeguard crucial system boot processes. It offers a tamper-proof, hardware-based root of trust that acts as a reliable detection mechanism to check the accuracy of the first and most important system BIOS code that the processor executes.
How Hardware-based Security from Dell and Intel Differs
Attackers shift to softer targets as one assault surface becomes more difficult. The supply chain and the below-the-OS layers are two examples of these emerging vectors today. Having hardware-based, built-in security incorporated throughout your fleet will help your business develop device trust and defend against these fundamental assaults, helping you stay one step ahead of bad actors. Intel and Dell are available to assist.
With defenses for every layer of the compute stack, our combined knowledge and co-engineering partnership enable us to assist enterprises in fending off particularly persistent and aggressive attacks. Learn how Dell and Intel collaborate to safeguard the workspace by reading our white paper.

[…] the 480 MB L3 cache of basic Genoa or the 1.5 GB cache pool of Genoa-X, it is a promising start for Intel’s attempt to catch up to the other companies in the […]
[…] Z790 MAX motherboards all come pre-installed with a brand new BIOS function that the company refers to as “P-Core Beyond 6 GHz.” This feature is exclusive to these […]
[…] brand new AMD AGESA 1.0.8.0 BIOS for AM5 motherboards has been made available by ASUS and is now being distributed. This update is […]